Security orchestration enables organizations to combine automated actions to achieve larger goals or implement more complex processes. By linking these tasks and tools into cohesive workflows, teams can respond to incidents more quickly and consistently. In turn, this enables organizations to streamline various security tasks and improve the overall efficiency of their operations.
This article describes the best practices for integrating security orchestration into an organization. It is written for cybersecurity professionals and contains a series of practical examples.
Key security orchestration best practices
Security automation vs. security orchestration: What’s the difference?
Security automation and orchestration are often discussed in tandem, but they serve distinct purposes within security operations. Automation executes individual predefined tasks efficiently, while orchestration connects multiple automated tasks into cohesive workflows. These workflows may handle specific processes end-to-end through automation and orchestration alone, or they may involve humans at various stages. By combining automation, orchestration, and human intervention, workflows can prompt relevant personnel for additional information when needed.
Security automation: Best for linear and isolated tasks
Security automation focuses on executing individual security actions without human intervention. It usually occurs between a few applications with a clear linear flow and typically involves straightforward, rule-based responses.
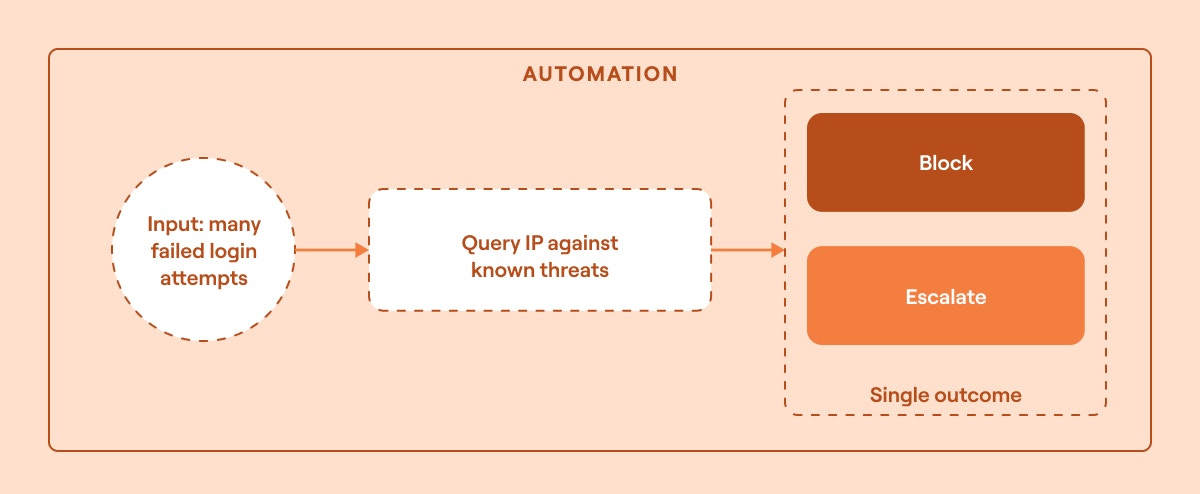
Example: A security and information event management (SIEM) system detects multiple failed login attempts from a single IP address, potentially indicating a brute-force attack. This suspicious activity triggers an automated workflow that queries the IP against known threat feeds. Based on this information, the IP is either automatically blocked by the IPS and firewall or sent to an analyst for manual review.
Why this is a security automation task:
Linear task: It involves a single decision point (block or escalate).
Minimal coordination required: No multi-team or multi-tool interaction is needed.
Fast and easily repeatable: It can be executed indefinitely without manual intervention.
Security automation description (source)
Security orchestration: Best for complex and dynamic workflows
Security orchestration uses automation as a tool or a building block but adds coordination, complex decision-making, and multi-step workflows. It involves managing interaction across multiple tools, teams, and data sources to ensure that security actions can be developed and carried out in a broader context. It can also include parallel execution, conditional logic, and adaptive responses based on the evolving security landscape.
Workflow orchestration and automation for security teams
- No code or low code - no custom development necessary
- Integrates with all your systems - internal and external
- Built-in safeguards like credential management and change control
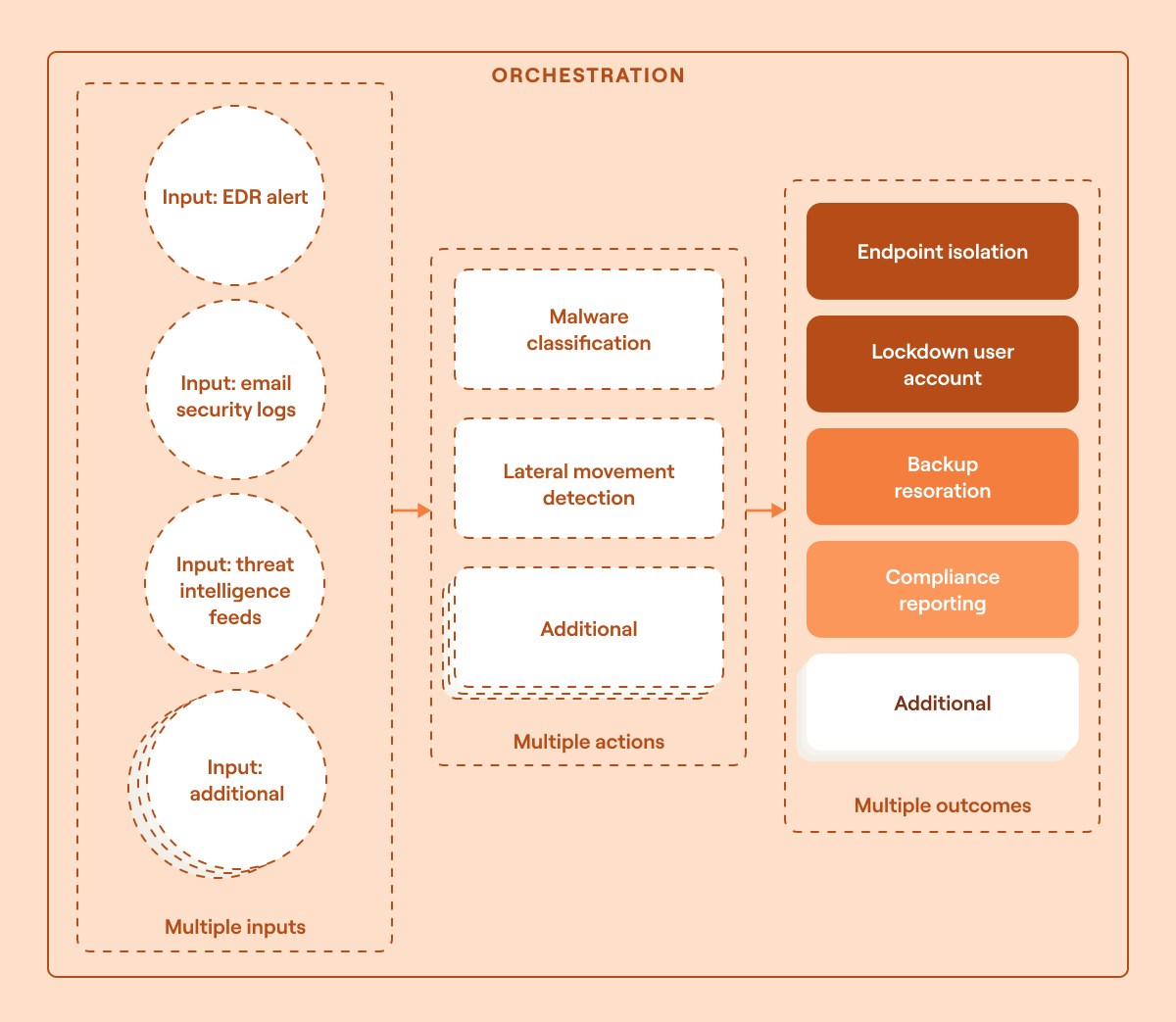
Example: A secure endpoint is infected with ransomware after a user opens an email attachment from an unknown sender. This triggers a security orchestration workflow that works to coordinate multiple security tools and teams to respond to the incident.
Why this is a security orchestration task:
Dynamic and non-linear workflow: The response varies based on many factors, such as attack severity, asset criticality, and backup availability.
Multi-tool coordination and multi-team collaboration: It requires integration among many security tools and involves many teams to fully respond.
Parallel execution: Different actions, such as containment, investigation, and user notifications, happen simultaneously rather than in strict sequence.
Human in the loop: The task requires a combination of automated steps and human oversight to successfully assess the incident.
Security orchestration description (source)
Automate routine, high-frequency tasks first
Security orchestration relies on the inputs and outputs from one or more security automation tasks. Therefore, it is essential to implement these tasks first.
Start with the boring stuff—particularly repetitive, low-complexity tasks that are tedious for humans but ideal for automation. Some examples might be enriching alerts with threat intelligence, tagging suspicious IP addresses, or collecting logs from security tools. While these tasks may not be glamorous, they form the building blocks of any effective orchestration strategy.
Starting with routine tasks provides a stable foundation. It helps make workflows more predictable and sets the stage for future orchestration. It’s not about doing less—it’s about laying the groundwork to do a lot more, a lot faster.
Example: Automating phishing alerts and reports
Scenario: A user reports a suspicious email to the company’s security team. Instead of manually reviewing each report, an automated pipeline is triggered to handle the initial investigation. This job might be automated using the following steps:
Trigger: A user reports an email as suspicious via their organization’s enterprise security portal.
Extract indicators: The orchestration and automation system pulls key email data such as the sender address, email subject and body, attachments and links, and IP addresses from headers.
Check open-source threat intelligence: Compare extracted indicators against known threats and vulnerabilities:
Compare data against known threat databases like VirusTotal, OpenPhish, or AbuseIPDB.
Identify whether URLs are malicious, including tactics like tabnapping, DNS poisoning, or session hijacking.
Use sandbox analysis tools like Cuckoo Sandbox, Filescan.io, or Volatility to scan attachments.
Note: Check out this example of an existing workflow for analyzing key aspects of phishing emails.
Analyze phishing email senders, URLs, & attachments
Analyze some key aspects of phishing emails in services like VirusTotal, URLScan.io, and Sublime Security across multiple Story forks.
Tools
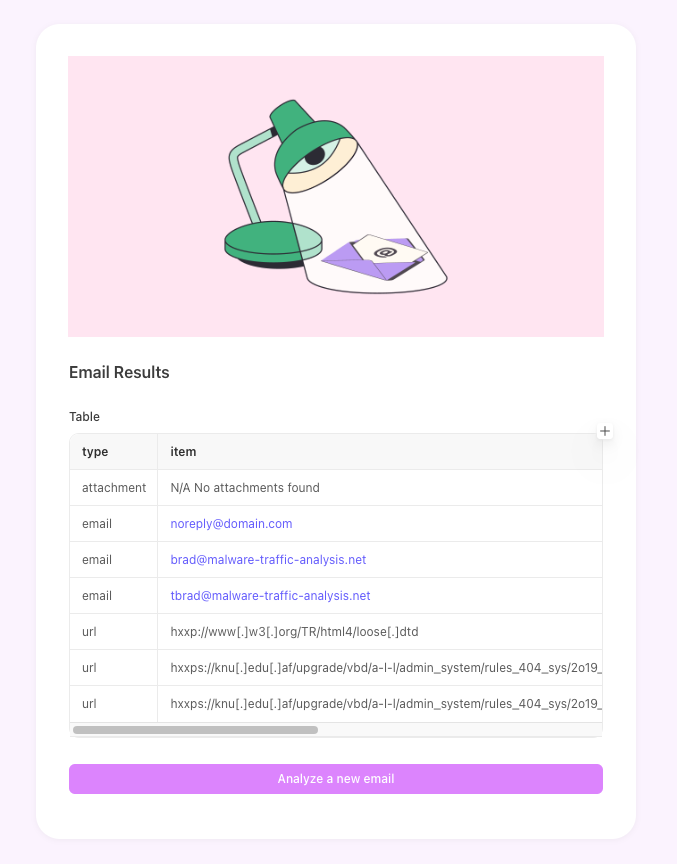
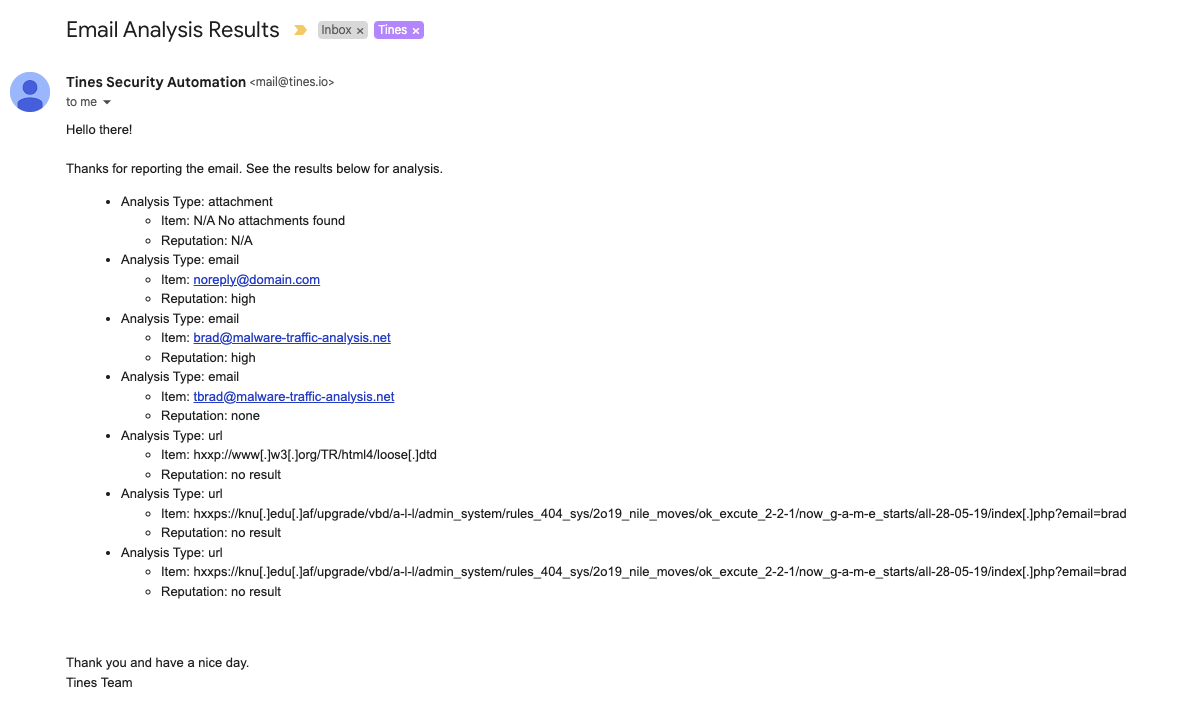
4. Automate decision-making: Use the outputs collected from security tools to decide how to respond to the report appropriately.
5. Document the incident: Create documentation of the incident, the analysis data, and the decision. If needed, create a ticket in a case management platform. Notify security analysts of the findings and recommended actions.
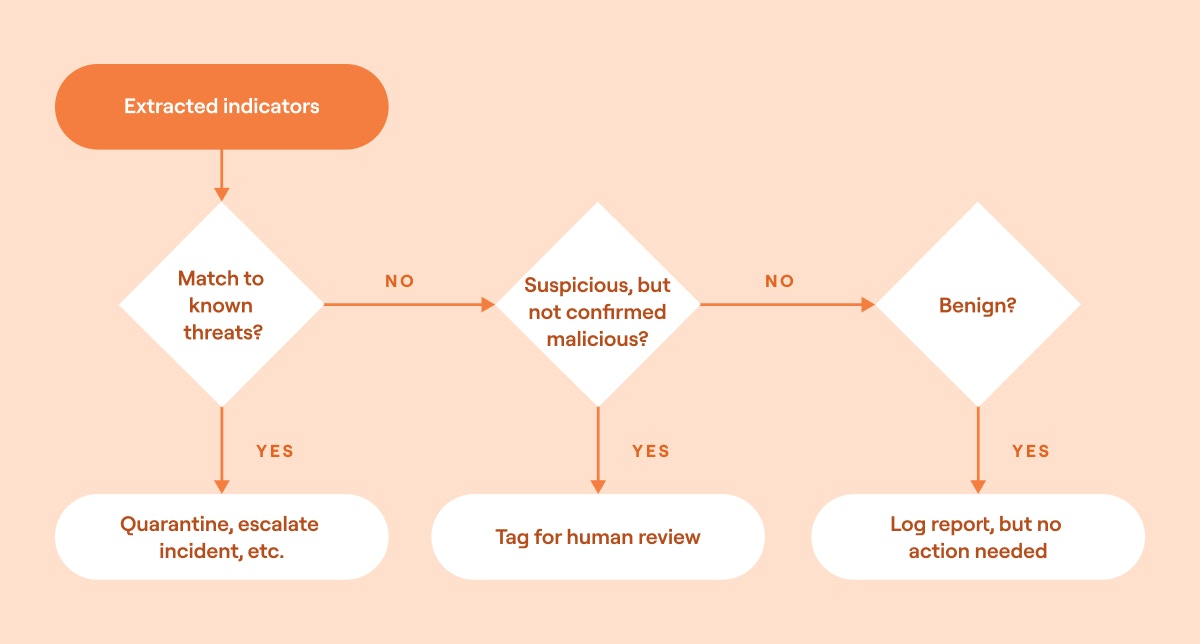
Automated phishing security orchestration example (source)
Choose one or two core use cases to get started
Security orchestration is inherently complex because it is a multi-team, cross-functional effort that requires a high level of coordination and collaboration. Rather than attempting to orchestrate everything all at once, start with a couple of well-defined use cases that naturally require cross-functional collaboration.
These up-front efforts can lay the groundwork for broader adoption. They can also help teams develop ways to align processes, refine integration points, and build confidence in creating orchestration workflows before scaling to more significant issues across the organization.
See Tines’ library of pre-built workflows
Example: Orchestrating incident response for newly-released vulnerabilities
Scenario: A new critical CVE that affects software dependencies in a cloud-based application is published. The response to this finding requires coordination across multiple teams, such as SOC, developers, DevOps, and compliance teams.
Trigger: A new CVE is published and detected in the cloud workload by a vulnerability scanner.
Gather intelligence: Use available resources to research and validate findings by:
Checking threat intelligence feeds and databases for known exploits
Identifying affected cloud assets such as containers, VMs, and web services
Cross-referencing the organization’s asset inventory to determine which mission-critical systems may be affected by exploits.
Automate decision-making: Choose how to respond based on information from intelligence gathering.
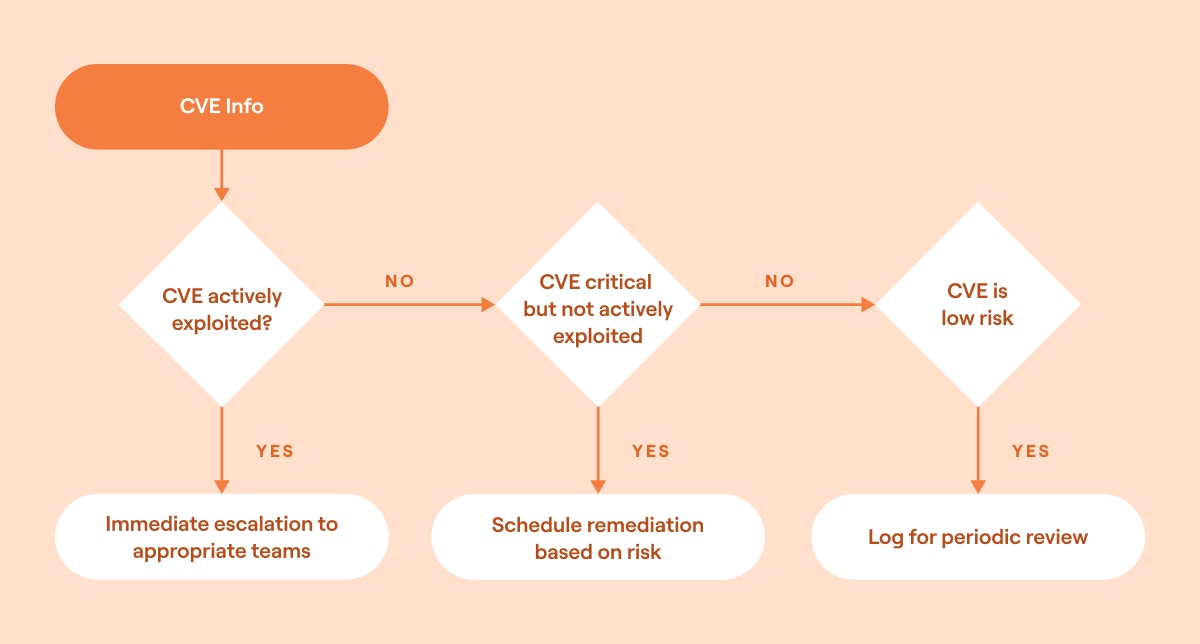
Decision making in security orchestration example (source)
4. Coordinate across teams: Have various teams assess the breadth and depth of the vulnerability:
Security team: Confirm exploitability, attack surface, and mission-critical devices.
DevOps: Deploy patches or mitigations in CI/CD pipelines.
Developers: Assess application impact, check for affected libraries, and update dependencies.
Compliance: Log incident and remediation efforts for security auditing.
5. Automate remediation and monitoring: Implement remediation steps and continually monitor for further impacts.
Note: See this workflow for an example of how to check for review-modified CVEs for new signs of exploitation.



Check updated CVEs for exploitation using VulnCheck and GreyNoise
Review all modified CVEs for new signs of exploitation. Obtain up-to-date CVE lists from VulnCheck and compare them against GreyNoise's real-world CVE exploitation data. A summary of the findings, including IP addresses to be blocked, will be provided.
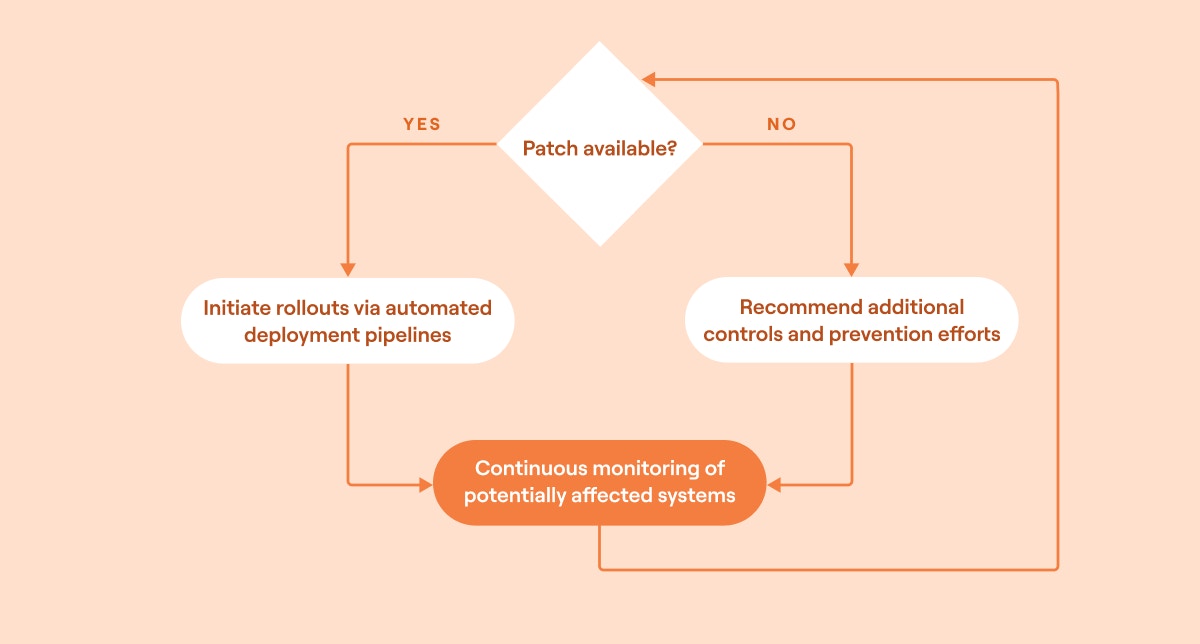
Security orchestration with automated remediation and monitoring example (source)
6. Conduct post-remediation validation: Make sure the recovery was successful and reduce the likelihood of a repeat incident:
Perform security testing to ensure that fixes are effective.
Update threat detection rules and training data to look out for related attack patterns.
Generate compliance reports for security auditing and future incident response management.
The table below contains some ideas and questions to ask to help identify core use cases in your organization.
Standardize data and API interactions
Data comes in various shapes and sizes. Security tools generate logs, alerts, and API responses in widely varying formats, which can cause issues when integrating them across systems. To ensure that orchestration workflows run smoothly, it is important to create data standardization frameworks that normalize inputs and outputs. This upfront coordination helps simplify integration across multiple tools and platforms.
Problem: Your team is responsible for orchestrating security alerts from multiple tools (SIEM, EDR, IDS), but the alert data formats are inconsistent.
The table below illustrates how common security tools—SIEM, EDR, and IDS—use different field names to represent the same types of data, making integration and orchestration challenging.
Solution: Normalize the data.
To support orchestration, it's important to normalize these fields. The table below shows a standardized schema that maps inconsistent field names from each tool to a common format for seamless processing.
Note: Use available tools to standardize data.
Solutions like AI in Tines are great for transforming raw alert data into a standard schema to ensure consistency before any other part of the orchestration workflow kicks off. Use a Transformation Action to normalize fields across tools to ensure that all security events follow a single format regardless of source. Here’s what a Tines JSON Transformation configuration for the example above might look like:
{
"source_ip": "{{$.src_ip || $.sourceAddress || $.remote-ip-address}}",
"event_timestamp": "{{$.timestamp || $.eventTime || $.detection-time}}",
"alert_type": "{{$.event_type || $.threatGroup || $.finding-category}}"
}Balance security orchestration with human review
Security orchestration and automation is great for handling simple, high-volume tasks, but it will never be a replacement for human judgment. Critical thinking and nuanced decision-making still require human oversight, especially when the stakes are high. It’s essential to keep humans in the loop, reserving orchestration and automation for what it does best while allowing security professionals to make the final call on high-impact issues. And even when automation is used, always verify the outputs it produces.
Continually monitor, optimize, and expand
Security orchestration and automation are not static processes: They require constant refinement to adapt to an ever-changing security environment. While both automation and orchestration reduce manual effort and streamline complex workflows, neither is ever truly “finished.” Technology and security are constantly changing, so it is always important to review workflows regularly.
Design modular workflow components that can be reused and modified as security evolves. Use real-world insights to improve orchestration, especially, drawing from incident post-mortems, analyst feedback, and threat trend analysis. Make sure workflows are regularly tested in realistic scenarios to help identify gaps and ensure that responses remain effective as conditions change. Continuous tuning not only strengthens your security posture but also ensures that your orchestration strategy scales with the organization’s needs.
Did you know Tines' Community Edition is free forever?
- No code or low code - no custom development necessary
- Integrates with all your systems - internal and external
- Built-in safeguards like credential management and change control
Final thoughts
The successful implementation of security orchestration requires strategic planning, continuous refinement, and cross-team collaboration. While automation is well-suited to handling isolated, linear, and repeatable tasks, true security orchestration brings together tools, teams, and decision points to create dynamic security workflows capable of handling complex security threats as they evolve.
Key takeaways:
Security orchestration is more than automation. It combines multi-tool, multi-team collaboration and coordination with complex decision-making to handle threats effectively.
Start small, then scale. Focus on a few high-impact use cases, refine workflows, then expand from there.
Standardization is essential. Normalizing security data across tools ensures that workflows function consistently.
Balance speed with control. Automate where possible, but keep humans in the loop for high-impact security decisions to prevent unintended disruptions and mitigate risk.
Security is never “set and forget.” Continuous monitoring, testing, and optimization are necessary to adapt to evolving threats and technology.