Few would argue that zero trust has become one of the most important principles of modern cybersecurity programs. But ever since the concept of zero trust security was first popularized by Forrester in 2009, many federal government agencies in the United States (along with private sector companies) have struggled to understand its requirements and implement it effectively.
Critically, zero trust does not represent a single security method or a type of technology. CISA’s zero trust framework outlines a set of security practices that should be part of most organizations' efforts to continually improve their cybersecurity posture.
A big part of improving zero trust security is in deploying the right zero trust technologies. But the market for zero trust security is sprawling and often confusing, as highlighted by Gartner.
“Zero trust is being misused as a marketing term. Vendors are applying the term ‘zero trust’ to market everything in security, creating significant marketing confusion.”
Gartner
Zero trust has many technology categories, with many products for every category. To further complicate matters, all the technologies in a zero trust stack should be able to work together to provide holistic control and comprehensive visibility.
To help address these challenges, we’ll discuss key considerations for how federal agencies should approach building their zero trust technology stack, as well as defining some of the most important technologies that support zero trust security practices.
6 things to consider when building your zero trust technology stack
Perhaps the most important and useful document on zero trust security is the zero trust maturity model published by the Cybersecurity and Infrastructure Security Agency (CISA) of the United States federal government.
It defines five technology pillars that organizations must address to advance their zero trust architecture. These include:
Identity
Devices
Networks
Applications/Workloads
Data
In addition to building up the zero trust capabilities of individual technology pillars, CISA emphasizes that agencies must also create a foundation of cross-pillar coordination to provide holistic cybersecurity management. These cross-cutting capabilities include:
Visibility and analytics
Automation and orchestration
Governance
While offering essential guidance for building zero trust security functionality, the CISA model can seem overwhelming for many organizations, especially for federal agencies with limited staff, expertise, budgets, and technology resources.
Here are some tips for how your federal agency can prioritize its zero trust technology purchases.
1. Establish a baseline
When figuring out what technology you need to improve your zero trust defenses, start by understanding what technologies and capabilities you already have.
If you haven't already done so, conduct a full inventory and assessment of your current security tools and IT systems.
2. Focus on removing siloes
While federal organizations need to advance the maturity of each zero trust pillar, they must also build out their cross-pillar capabilities for visibility/analytics, automation/orchestration, and governance.
Critically, many federal organizations use custom GOTS (government off-the-shelf) applications and technologies, as well as an array of COTS (commercial off-the-shelf) tools, making integration of these disparate technologies challenging.
Ideally, the tools used for cross-functional coordination must be able to work with any and all the tools in your zero trust tech stack and IT infrastructure (now or in the future).
3. Consider your environment
The effectiveness of your zero trust investments depends heavily on your tech stack's ability to work within your hosting infrastructure. This presents unique challenges, in particular, for agencies leveraging hybrid cloud architectures, or those managing classified or completely air-gapped networks.
In these and many other cases, tools that are hosted on a shared stack fall short. Look instead for solutions that offer deployment options to suit your hosting environment - self-hosted, on premise, etc.
4. Determine your unique requirements and priorities
Now that you understand what you already have in place, you should be able to identify what’s preventing you from advancing your zero trust maturity across the pillars and cross-functional capabilities. Next, it’s time to find the technology that will help you plug those gaps.
This is a good time to identify which aspects of zero trust have the potential to make the most positive impact on your program, relative to their cost and complexity to deploy and integrate. These should become your priorities, and will result in the greatest return on investment for your efforts.
100% compliance is an unrealistic, and therefore unhelpful, goal. Zero trust isn’t a checklist to complete, it’s a living program that requires constant improvement and innovation. This is yet another reason why we need our technology to be flexible, adaptable, and scalable. These systems should help us evolve, not create barriers to progress.
So, before you go shopping, ask yourself these questions:
Which aspects of zero trust are most important to your organization?
What are the biggest vulnerabilities in your security posture that need to be addressed?
Where is your current technology letting you down?
What is your hosting infrastructure - self-hosted, on-prem, cloud, or hybrid?
How well does your technology communicate?
What's the level of effort to get information from one system to another or to export it for auditing purposes?
How efficiently can your team find what they need?
Do you have visibility across all of these systems? What could help with that visibility?
5. Let the buyer beware
With a shopping list in hand, federal agencies need to keep in mind that the zero trust technology market is extremely complex, filled with hype and overreaching claims by vendors.
It’s important to remember that you can’t buy zero trust out of a box. There is no all-in-one solution that works for every team. Your zero trust program needs to be intentionally designed and tailored for your specific organization and mission set.
Build out a detailed checklist of needed capabilities before shopping for new tools. Any technology must clearly address these specific security requirements before it is even considered for a shortlist.
6. Select specific use cases for evaluation
Once you’ve created a shortlist of products, it’s time to put them to the test. Collaborate with your team to establish mission-critical use cases that will help you evaluate your vendors.
Don’t go easy on your vendors - choose workflows that are currently draining resources, touch multiple zero trust pillars or require multiple systems to speak to each other. And make sure to use the same use case when evaluating vendors in the same category, so you can compare like with like.
Your zero trust security tech stack: the essentials
Let's take a closer look at the key technologies and frameworks to consider when building out your zero trust technology stack. First, we'll see how these technologies and frameworks map directly to the zero trust pillars and cross-cutting capabilities:
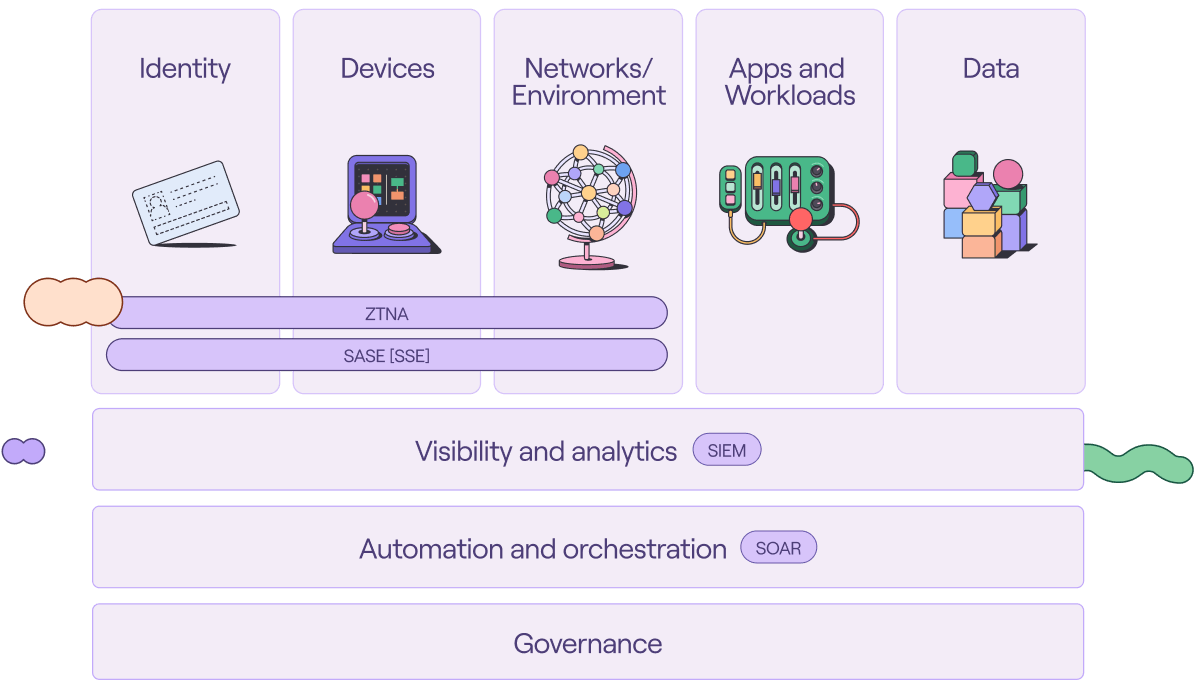
Mapping your tech stack to zero trust pillars and cross-cutting capabilities
ZTNA is the first step into zero trust. It overlays the identity, device and network/environment pillars.
SASE is the product or suite of products that works with the tools implemented as part of ZTNA to further protect the perimeter.
Essentially, ZTNA 2.0 would also cover application workload and data.
SSE looks to be a subset of the SASE framework.
SIEM falls under the visibility and analytics cross-cutting capability.
SOAR falls under the automation and orchestration cross-cutting capability.
Now, let's look at each technology and framework in greater detail:
Zero Trust Network Architecture (ZTNA)
ZTNA replaces traditional perimeter-based security models with a dynamic, identity-centric framework that enforces strict access controls and continuously verifies and validates every access request. This access is granted based on the principle of least privilege.
So rather than building a massive wall around the perimeter of the network to prevent intruders, ZTNA assumes breaches will happen and relies instead on locking the virtual doors in all the rooms of a computing environment to limit the scope of a breach. A common way this is addressed is through network micro-segmentation.
Security Access Service Edge (SASE)
SASE technologies converge wide area networking (WAN) and security functionalities into a unified cloud-native architecture that is delivered as a service.
SASE incorporates zero trust principles and helps organizations implement secure access policies based on user identities, device health, and contextual factors across both traditional enterprise networks and dynamic cloud services. This ensures that only authorized users and devices can access sensitive resources, regardless of their location.
The most common example of SASE technology is software-defined wide-area networks (SD-WANs).
Security Service Edge (SSE)
SSE technologies, as part of the SASE framework, provide integrated, cloud-centric capabilities that facilitate secure access to websites, software-as-a-service (SaaS) applications, and private applications.
SSE supports the modern distributed and mobile workforce by enabling secure access to resources from any location while maintaining a consistent security posture.
Examples of SSE technologies include cloud access security brokers (CASB) and firewall-as-a-service (FWaaS).
Security Information and Event Management (SIEM)
SIEM refers to a set of technologies and processes used to collect, analyze, and correlate security event data from various sources throughout an organization's IT infrastructure. By implementing SIEM, organizations can improve their ability to detect, investigate, and respond to security events in a timely manner.
SIEM helps enhance an organization's overall security posture, enables proactive threat hunting, and supports regulatory compliance efforts.
Security Orchestration and Response (SOAR)
SOAR technologies provide a set of tools and features that automate cyberattack prevention, investigation, and response. They aim to streamline and enhance security operations by integrating and coordinating separate security tools into cohesive workflows.
Traditional SOAR platforms typically rely on an app-based integration model. Unless your vendor of choice has already built the specific integrations you require, these types of connections can take a lot of time and effort to develop and maintain.
A truly effective SOAR platform is only as strong as its weakest link. If it's not compatible with all the tools in your zero trust technology stack, or can't perform a desired action in that tool, then it might not work at full capability when a cyberattack hits your organization.
Tines is a workflow builder that offers a modern approach to SOAR, allowing security teams to connect any tool or system with an API, internal or external. This gives organizations ultimate flexibility for how they build their zero trust technology stack.
🪄Tip
Continuing your zero trust journey
The demands of zero trust security are significant. But zero trust is essential to improving the digital defenses of federal agencies.
By using the CISA zero trust security model, prioritizing efforts based on your organization's unique needs, and steadily adding capabilities over time, federal agencies can efficiently build a robust security program for protecting against modern cyber threats.