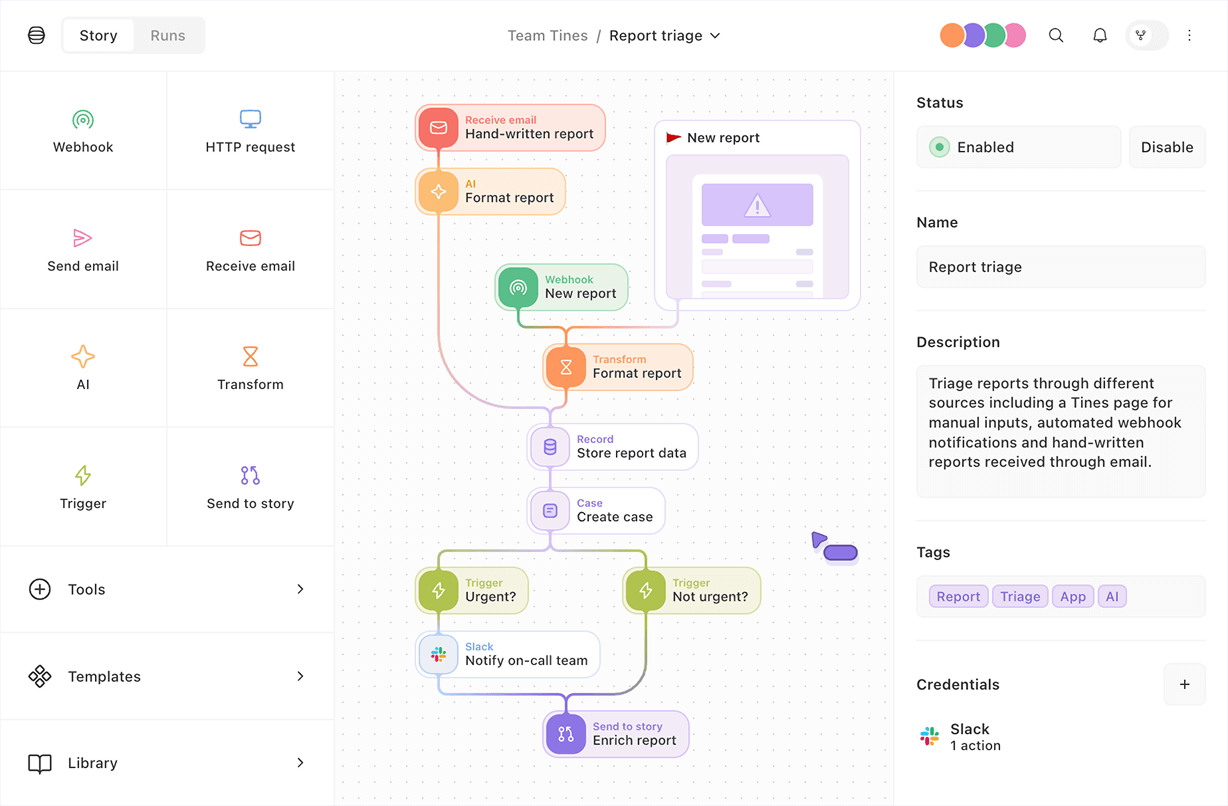
Manual threat intelligence processes leave your security team drowning in alerts, missing critical threats, and racing against attackers who don't wait - orchestrating and automating threat intelligence is your key to a proactive defense.
The good news? There's a Tines workflow for that.