There is an evolutionary shift happening within cybersecurity, one that looks to be of benefit to everyone.
Cybersecurity infrastructure is moving into the cloud. This creates a reduction in the IT workload for security teams, as it allows them to focus on protecting the organizations they serve, rather than maintaining countless points of vulnerability within a company’s hierarchy.
Cybersecurity tools are also becoming increasingly accessible, bringing a wealth of diverse talent into the field. It is no longer the domain of those with secret knowledge but rather something that anyone who chooses to can get involved in.
A side effect of these changes is that the traditional sales-heavy process involved in acquiring cybersecurity tools is becoming obsolete. The most interesting and innovative companies in this space offer some version of a self-serve model with a free tier. They have confidence that their solution offers enough value that, if made freely available, people will be able to see that value for themselves. This approach creates transparency, accessibility, and comprehensive benefit for all involved.
LimaCharlie, the company I work for, incorporates this model while embodying the principles listed. We make cloud-first cybersecurity tools and infrastructure built for massive scale - an approach familiar to anyone who has worked with Amazon Web Services or any other major cloud infrastructure provider. We offer endpoint detection & response (EDR), software-defined networking, log & artifact ingestion, and a growing list of adjacent capabilities. Our team knows that making it easy to access the platform allows people to see how much value it offers. This is why we have a full-featured free tier of two tenants, each with two endpoint sensors. This approach has been great for us and has allowed us to earn the community's trust.
In consideration of this, I am always interested in learning about other cybersecurity companies taking a similar approach.
Recently, I learned of Tines' free Community Edition. Excited by my initial exploration, I was further delighted to discover that Tines integrates with LimaCharlie's API directly, and this inspired me to see what I could accomplish with the two platforms working together.
One of LimaCharlie’s core benefits is the ability to alert security teams and automate actions on the computer when suspicious behavior takes place. These detections are made by analyzing events occurring on the endpoint and processing those events through a set of rules.
There are a lot of things you can use rules for, and the severity of detections varies dramatically. Sometimes a rule may trigger on a network scan. While this is something to note in the context of everything that’s happening, it might not be enough on its own to justify raising alarms.
However, seeing a new user on the network trying to access restricted files is certainly something you want to have an awareness of, regardless of when it happens. This is where Tines and LimaCharlie, together, can make magic.
For this demonstration, I am going to apply an open-source set of detection rules - the Sigma rule set - to my endpoints under LimaCharlie and then use Tines to automate the triaging of alerts being generated by these rules.
For those detections made which have a low-risk value, I am going to use Tines to create a ticket in Jira for the security team to look at as part of their regular process. For detections that are deemed to be of the highest risk category, I am going to send out an email, an alert to a Slack channel, and tell LimaCharlie to stop letting that computer communicate over the network, allowing for the exception of still being able to communicate with LimaCharlie.
Enable Sigma Rule Coverage
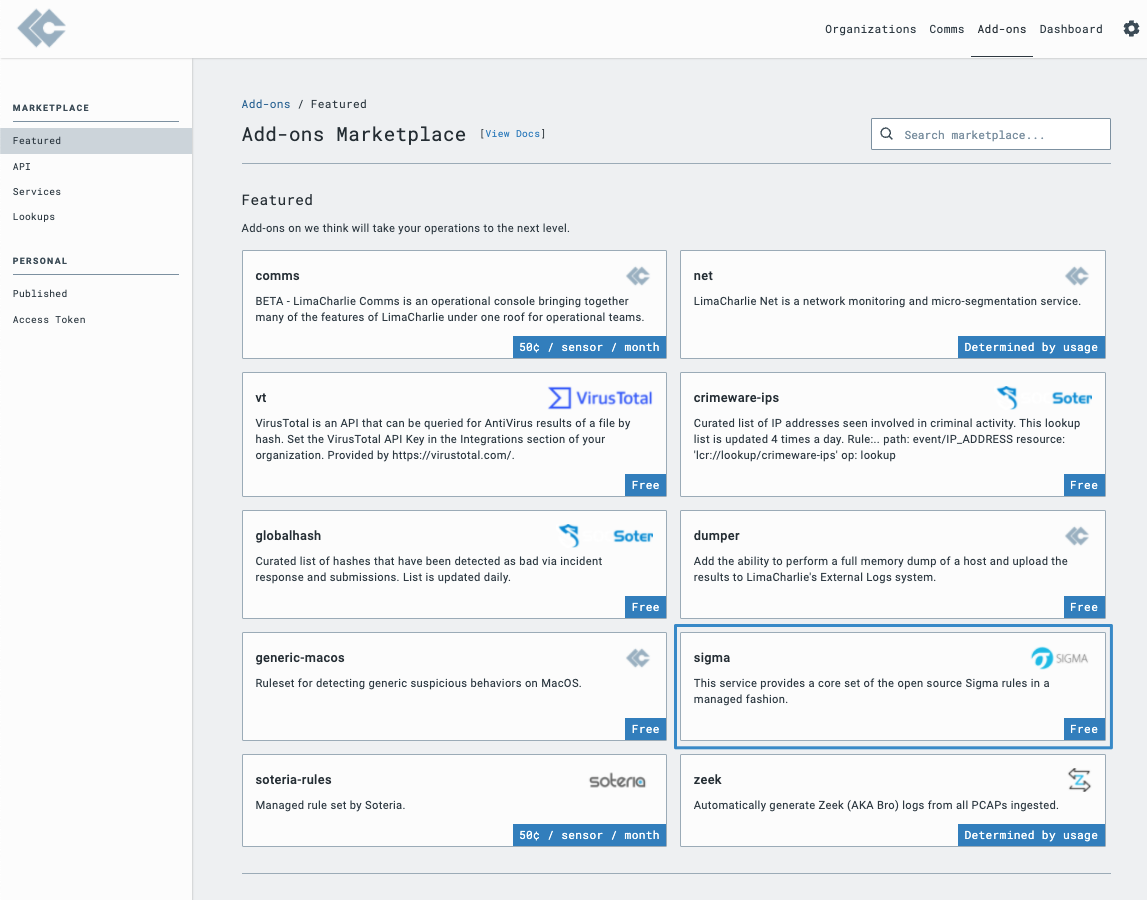
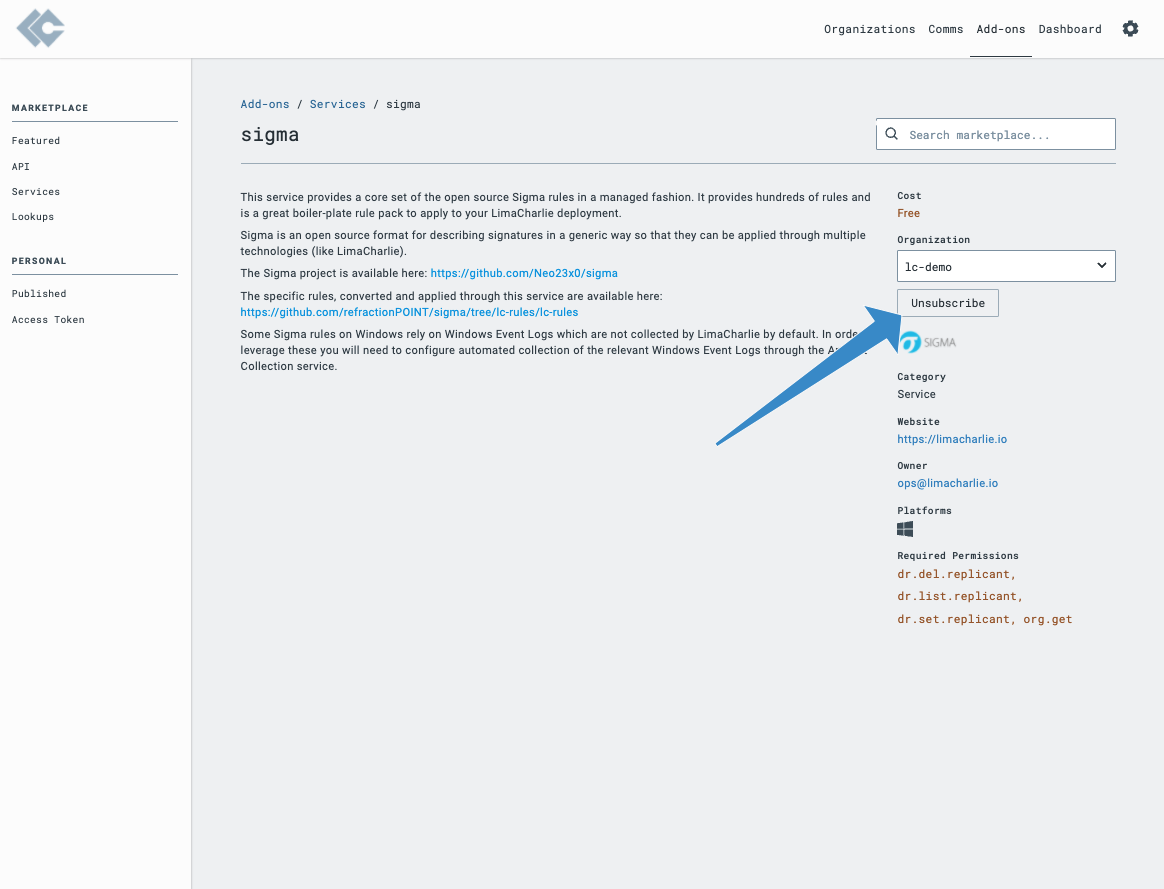
Assuming you already have endpoint sensors installed from LimaCharlie, you need to login into the web application and visit the add-on marketplace. Once in the Add-on marketplace, seek out the ‘sigma’ item and click on it. Once selected, simply click subscribe.
Your endpoints are now being monitored by hundreds of the open-source Sigma rules set in a managed fashion. More information on the Sigma project is available here.
Create Webhook with Tines
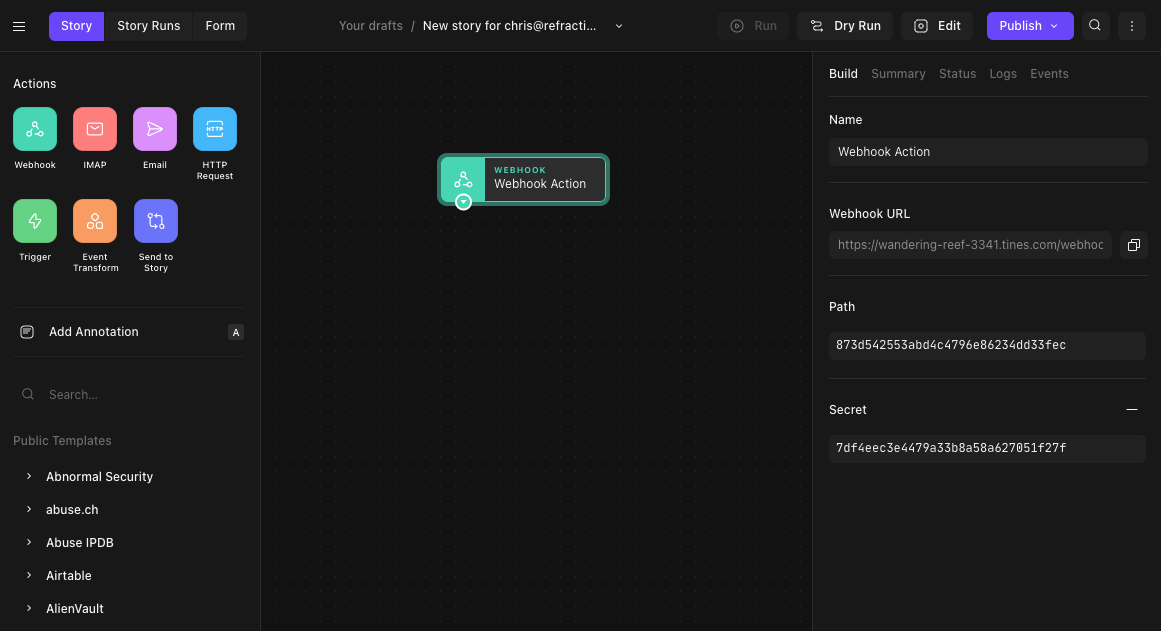
Inside of Tines, we are going to drag a Webhook Action onto our Storyboard, and then copy the Webhook URL and Secret from the right-hand menu.
Connecting the Webhook to LimaCharlie
With our Sigma coverage enabled in LimaCharlie and our Webhook Action created in Tines, the next thing we need to do is connect them. To do this, we are going to create an output in LimaCharlie by clicking on Outputs in the left-hand menu, and then clicking Add Output. This will open a dialog and allow us to configure the webhook.
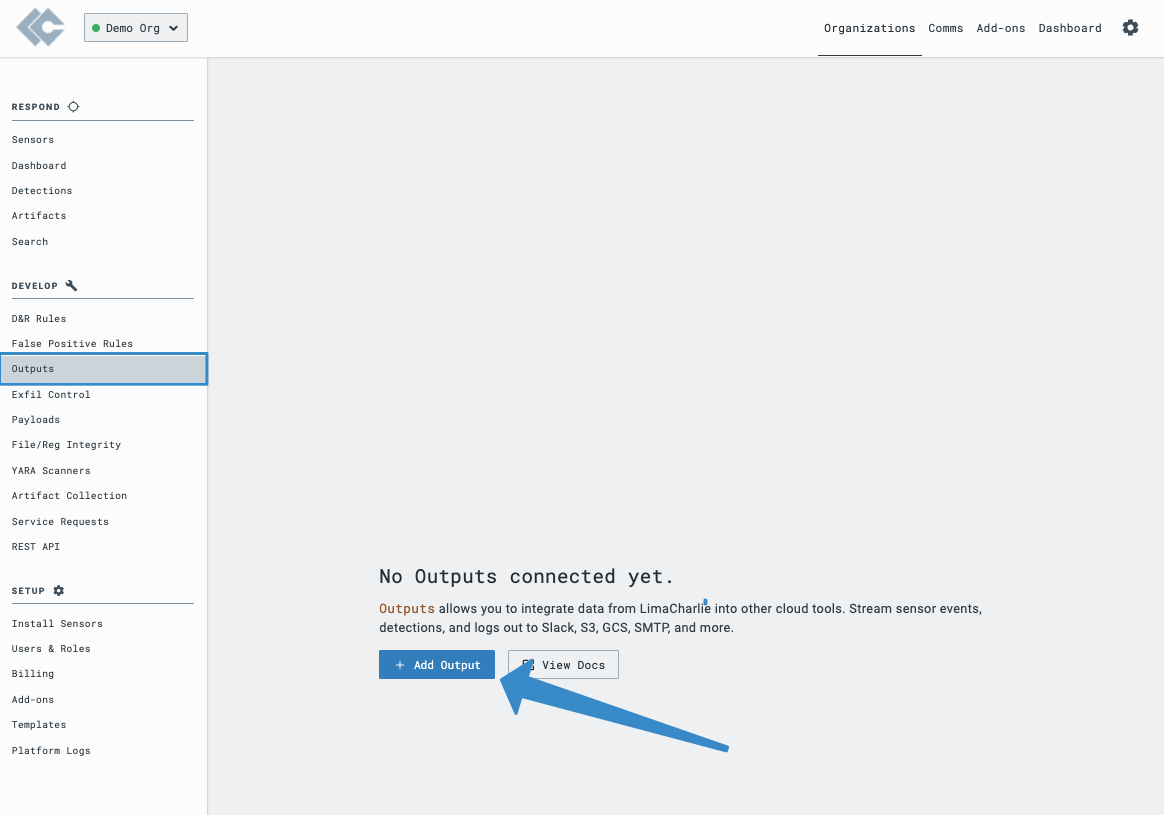
LimaCharlie offers several default streams of output telemetry, each of which can be further filtered through custom configuration. For this example, we are going to choose the Detections stream that will send event telemetry when detections from our Sigma rules set occurs.
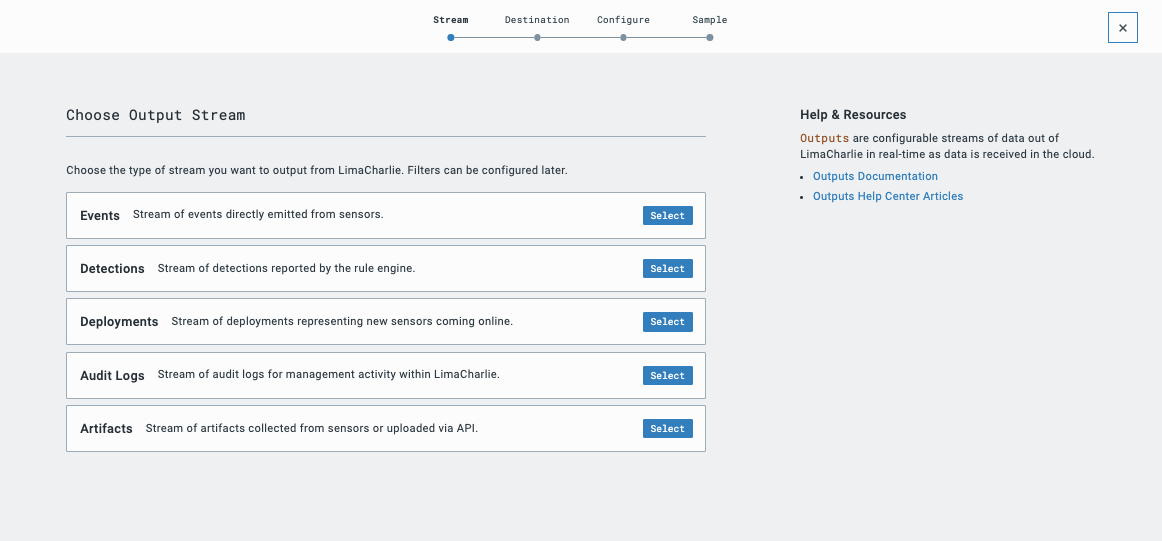
With Detections selected, we are going to choose Webhook from the list of default Outputs.
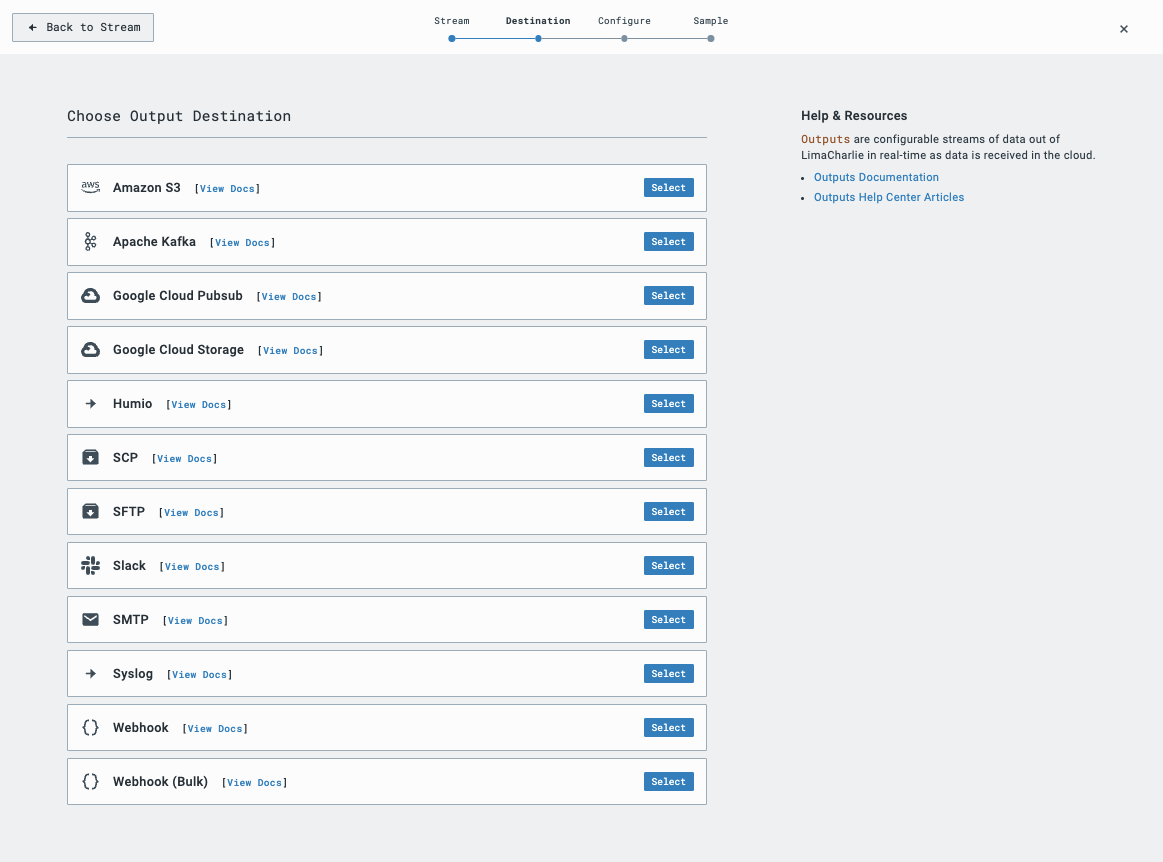
With Webhook selected, we will configure the Output. Give the Output a name that will remind you where the telemetry is going, then copy over the destination and secret from Tines.
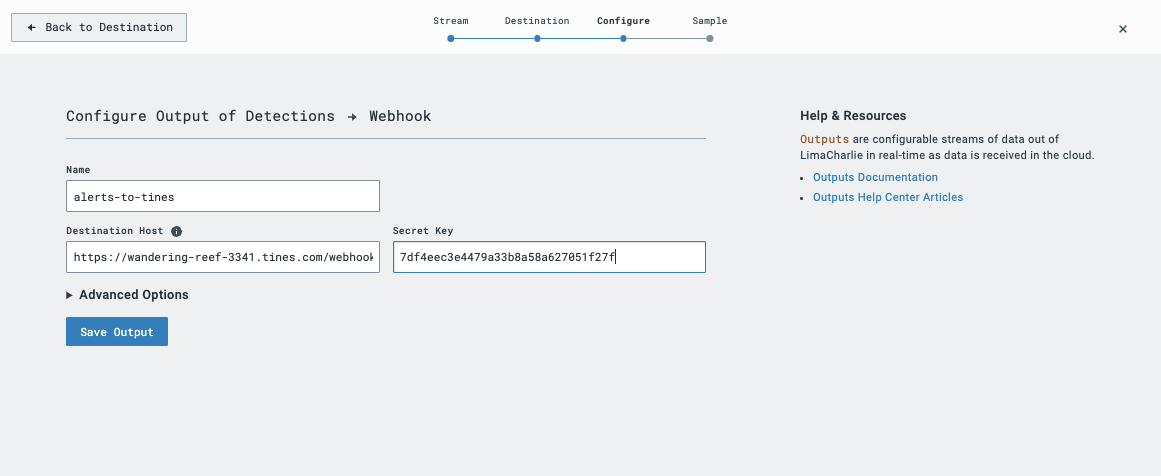
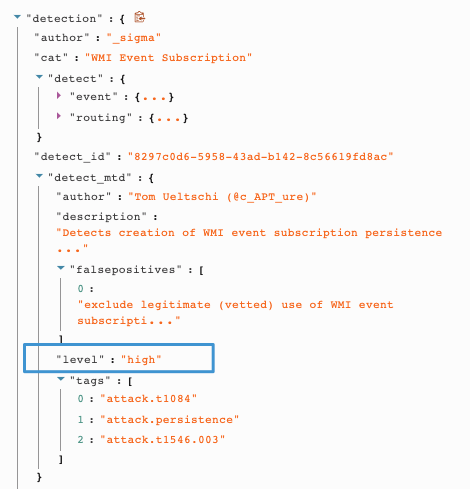
Create a Trigger in Tines
As part of their design, Sigma rules have a severity score associated with detections. With Sigma, detections are classified as either low, medium, or high. Using a Tines Trigger Action, we are going to examine the telemetry produced by the detection and route the Tines Story based on the severity. For detections that are low or medium, we are going to create a ticket in Jira for the security team to look at as part of their normal process. For the detections that are classified as high, we are going to ring the alarm and send out some notifications.
Create a Ticket in Jira
Using a Tines HTTP Request Action, we are able to easily connect to Jira and create a ticket whenever a Sigma detection is made with a severity level of low or medium.
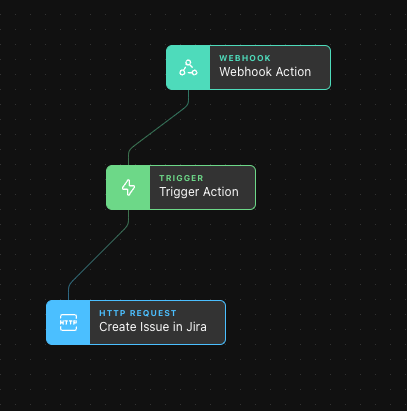
Send an Email and Alert to Slack
To create our high-level alert, we take a similar approach to what we did with setting up the Trigger for Jira, but this time we initiate an Email Action and an HTTP Request: Post Message to a Slack Channel.
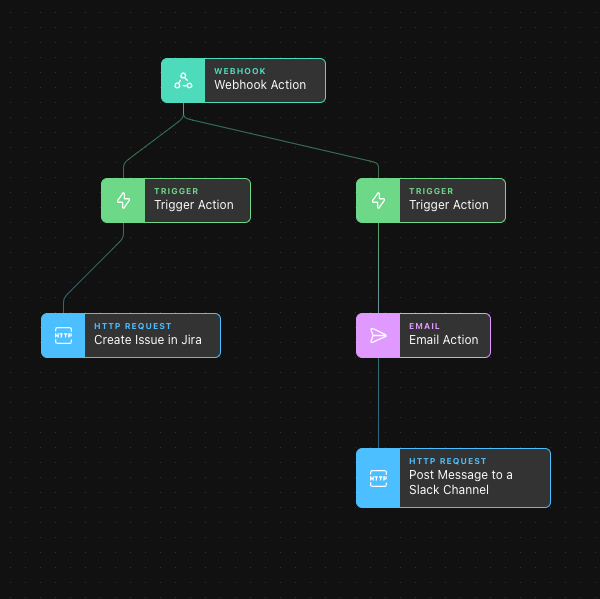
We are using email and Slack in this example, but it would be just as easy to use PagerDuty or any other cascading alert service.
Conclusion
This article outlined an example designed to demonstrate the effortless integration and powerful capabilities available from this new generation of cybersecurity vendors. If you have further curiosity about LimaCharlie, sign up for the full-featured free tier here or book a technical demo with our engineers here. You can also get started for free with Tines' awesome no-code security automation platform here.