Cloud security can be a daunting subject for groups just beginning to deploy in the cloud and for experienced veterans with sprawling cloud architectures. With all of the confusing features and service offerings from cloud providers, we at Tines are hoping to help narrow down the focus to a handful of high impact response actions that will help keep your organization out of the news.
Here, we will review setting up Tines to receive events from AWS services, automatically take action on them, and record the activities in a ticketing system.
Tines Webhook & AWS Simple Notification Service
Tines enables engineers to quickly and easily create HTTP Webhook destinations to send data of any kind with a simple web request using the Webhook Action in Stories. The best AWS service to enable the use of webhooks is the Simple Notification Service (SNS) which can relay events and alerts from many other AWS services. We've briefly covered it previously setting up AWS Security Hub which goes to show its flexibility. Let's review how to get set SNS up and pointed to a Tines webhook.
Keep in mind when performing these steps is the concept of 'regions' in AWS, lovingly referred to as us-west-2 or similarly formatted. Deploy many of these services in the same region as they cannot be accessed across different regions. Luckily, many organizations generally deploy to a single region.
Tines Webhook
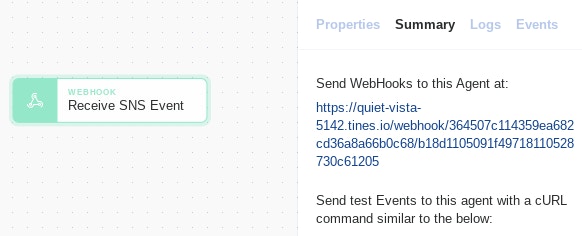
In your Story, simply drag a new 'Webhook' Action to the Storyboard.
Name the Action ('Receive SNS' in the below example). Make note of the webhook address for later.
Amazon Simple Notification Service
Find and navigate to the 'Simple Notification Service' in your AWS console.
On the left side, select Topics.
At the top right, select Create topic.
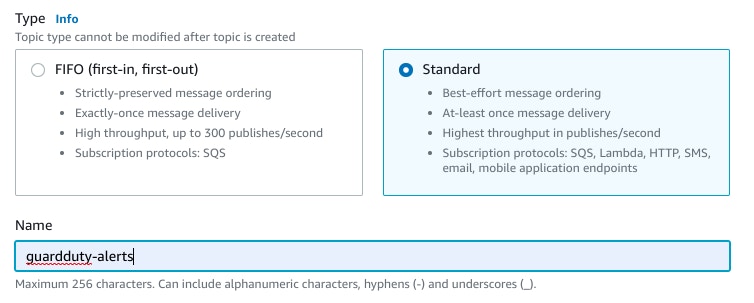
Under the 'Type' header, use the 'Standard' radio button. Name the rule ('guardduty-alerts' in the below example) and select Create topic to create the new topic.
On the left side, select Subscriptions.
At the top right, select Create subscription.
Under 'Topic ARN' select the Topic created in step 4. In the 'Protocol' drop down, select HTTPS. Under 'Endpoint' enter the webhook Action address created previously. Select Create subscription to create the new topic subscription.
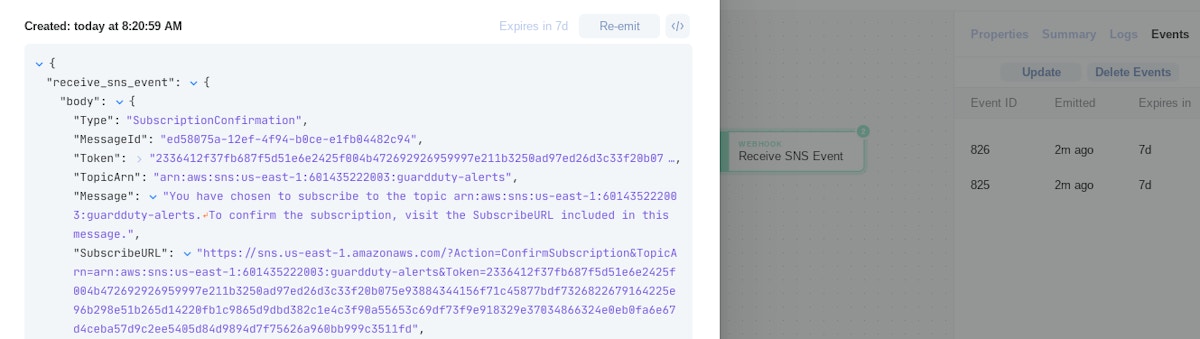
Once the topic subscription is created, AWS will send a confirmation event to the receiving webhook which includes a URL that needs to be visited to finish setup. Tines will receive that event and in the body of the message will provide the 'SubscribeURL' that can be entered into any web browser.
A linked HTTP Request Action could also be created and linked to the webhook Action to automate this step.
AWS GuardDuty and AWS CloudWatch
Now that we have a reliable way to send AWS events from nearly any service to Tines, let's go after capturing data from a valuable source of security alerts - AWS GuardDuty. GuardDuty can be thought of as an intrusion detection system for all things AWS, detecting compromised hosts to publicly available storage buckets.
If you don't have AWS GuardDuty enabled already, it is easy to activate by searching for the GuardDuty service in the AWS console and selecting "Get Started" → "Enable GuardDuty".
Just enabling AWS GuardDuty, unfortunately, does not send the events anywhere outside of the GuardDuty console. To link up AWS GuardDuty and our AWS SNS service (in order to send alerts to our webhook), we'll use AWS CloudWatch.
AWS CloudWatch allows for administrators to choose a class of events (in this case GuardDuty, but you can extend this configuration to many other services) and send them to AWS SNS.
Find and navigate to the 'CloudWatch' service in your AWS console.
On the left side, under the 'Events' heading, select Rules.
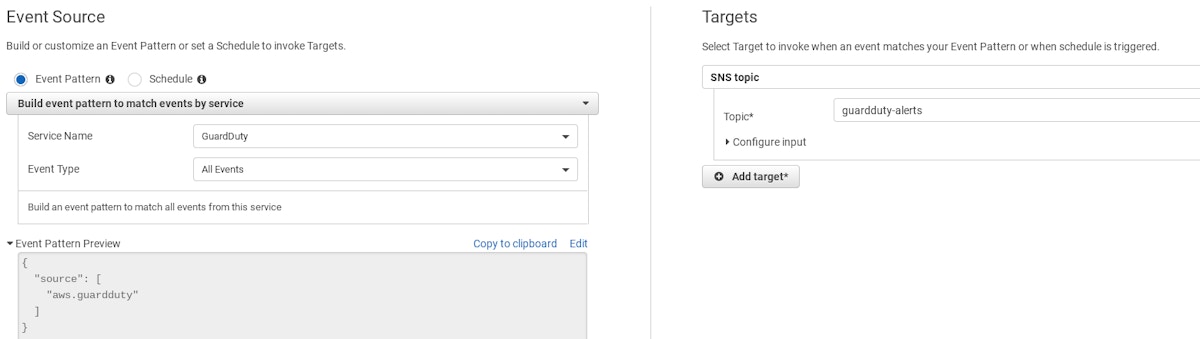
Select Create rule. Under the 'Event Source' header, use the 'Event Pattern' radio button. Select GuardDuty for the 'Service Name' and All Events for 'Event Type'.
Under the 'Targets' header, select SNS topic, and choose the topic created previously as the 'Topic'. Select Configure details.
Name the rule (perhaps 'guardduty-cloudwatch-sns') and select Create rule.
GuardDuty events will now begin to be identified by CloudWatch, sent to the SNS topic, and ultimately be sent to the Tines webhook.
Response Action to S3 Bucket Alerts
You've probably heard about an organization's data being leaked by having AWS S3 storage buckets open to the world. S3 buckets can pose a difficult balance of serving important business resources to consumers (documents, files, website content), but also not sharing too much. AWS Guardduty will detect when an S3 bucket has been opened to the world and we can respond to that alert automatically by applying a policy to tighten access to resources proactively. Let's dig in and extend our webhook to respond to some specific GuardDuty events.
IAM Credential
Find and navigate to the 'IAM' service in your AWS console.
On the left side, under the 'Access management' heading, select Users.
At the top, select Add user.
Fill out a user name (ex. tines-automation) and select the 'Programmatic access' checkbox. Click Next: Permissions to move to the next page.
At the top of the 'Set permissions' page, select Attach existing policies directly. Search for the policy 'AmazonS3FullAccess' and select the checkbox next to it. Click through Next: Tags, Next: Review, and Create user to create the IAM user.
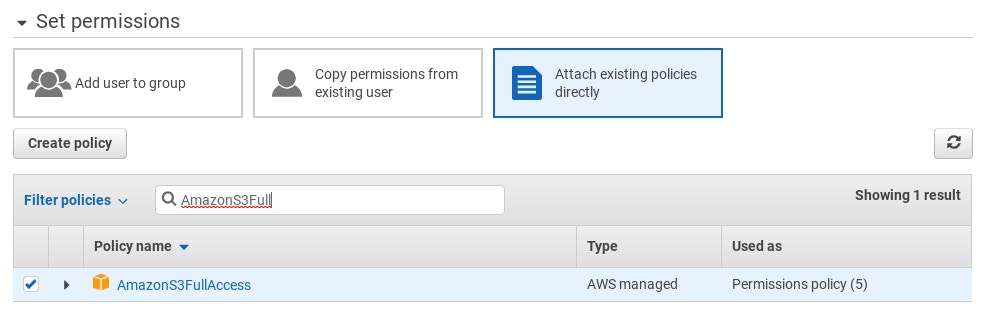
Record the 'Access key ID' and 'Secret access key' values for later.
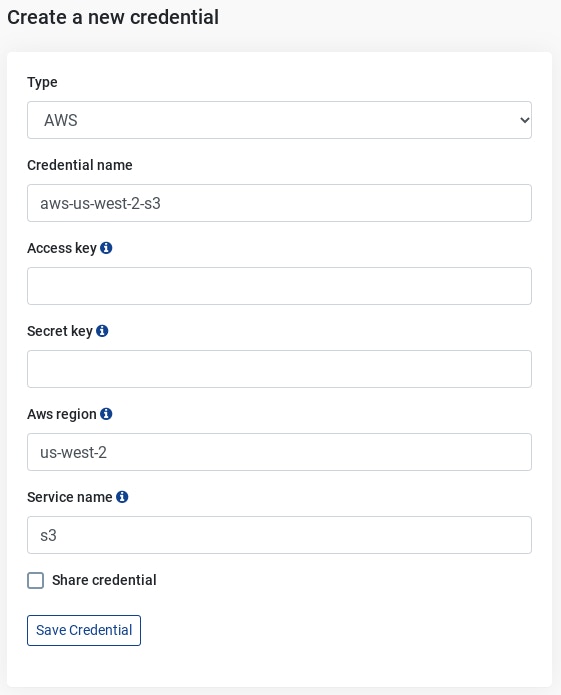
Tines Credential Setup
In your Tines tenant, navigate to 'Credentials' at the top of the page.
Select New Credential at the top right.
In the 'Type' dropdown, select AWS. This allows Tines to seamlessly handle authenticating to the AWS REST API. Fill out 'Credential name' with the variable name you will use in your Actions. Fill out 'Access key' and 'Secret key' with the information from the IAM credential created previously. Fill out 'Aws region' and 'Service Name' with the region where your S3 buckets are deployed and 'S3' as the service.
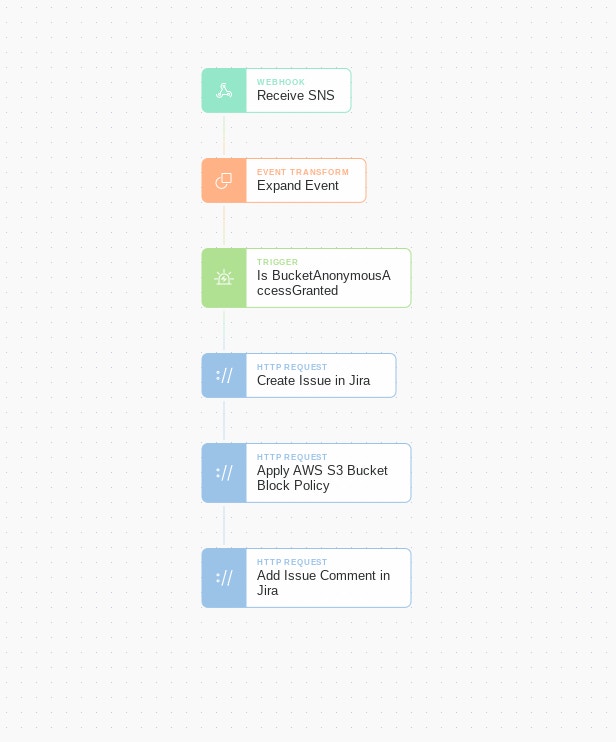
Tines Response Story
Extend out your Tines Story with the following:
An 'Expand Event' Action linked to the 'Receive SNS event' agent. The GuardDuty events sent by SNS are wrapped in metadata included by SNS, and the GuardDuty event will be in the Message field.
A 'Trigger' Action linked to look for and only take action on GuardDuty findings which are named "Policy:S3/BucketAnonymousAccessGranted". A full list of findings can be viewed here.
A Tines public template Action which makes an HTTP Request to the AWS REST API, setting the S3 bucket's public access policy in a 'deny all' fashion with S3 bucket information from the GuardDuty finding.
Creates a Jira ticket to track the alert which was received and updates it with the action taken.
Responding to public S3 buckets is just the beginning. Additional public Action templates that could be used for response actions include setting IAM credentials inactive, taking forensic backups of EC2 instances, (re-)activating CloudTrail logging, and isolating EC2 instances if compromised.
The Story used here can be downloaded imported into your tenant using our Story Library.
Loading story...
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*