The complexity of keeping organizations, customers, and employees safe from cyber threats increases every day. Security teams are often overwhelmed with the need to manage multiple workflows across a myriad of tools.
The combination of Humio and Tines helps customers build a clear picture of what's really going on within their environment and automate effective responses at speed and scale.
Humio is a purpose-built, modern log aggregation, storage, and analysis tool if you're not already familiar with it. Humio allows users to send and receive all relevant log data to create instant visibility in one solution. It also enables organizations to understand large amounts of computer-generated data and instantly pinpoint availability concerns, and identify security threats in their environment.
In this blog post, we'll outline how security teams can take full advantage of Humio's unrivaled real-time detection capabilities and leverage it alongside Tines to rapidly deliver automated containment actions that can significantly reduce the mean time to respond and prevent an incident from escalating into a full-blown breach.
How Humio and Tines work together
Tines can deliver automated responses to the real-time alerts generated by Humio as a result of detections and searches across all ingested log data. This can include correlations across multiple log types, and threat intelligence feeds.
With Humio and Tines, customers can automate actions based on events seen across different data sets and focus on the issues that matter most: improving your organization's security.
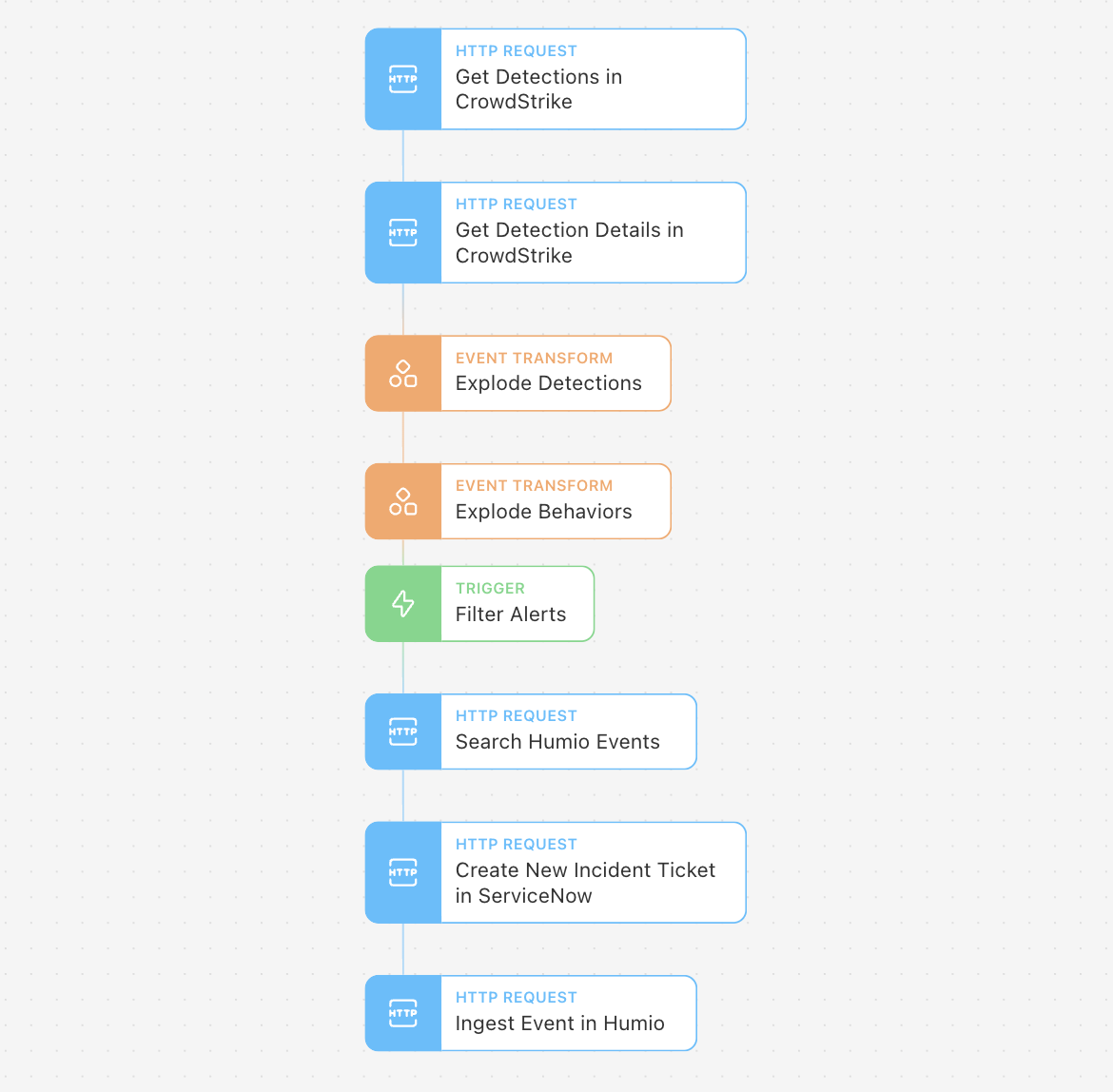
Sample Tines story working with Humio and CrowdStrike
In the scenario above, we've used an HTTP Request Action in Tines to query CrowdStrike for detections matching certain predefined criteria. This returns a collection of Alert IDs. We then query CrowdStrike to get more details about these alerts, including what the alert is, what machine it happened on, and the specific pattern of behavior.
We explode these detections using an Event Transformation Action to create one event per alert. CrowdStrike monitors for specific patterns of behavior to provide more granular information on what exactly happened on the endpoint, so we use another Event Transformation Action to break this data up into one event per behavior.
With a Trigger Action, we filter out false positives and any events that don't match our criteria before performing additional enrichment and searching Humio to check if the alert has occurred before. In this particular workflow, Tines automatically opens an incident in ServiceNow for someone to review it. Finally, Tines sends the alert to Humio to be stored, so it's easily searchable if it happens again in the future.
Preconfigured public templates are available within Tines for some of Actions used above, including:
Get Humio alert ID
Get Humio alerts details
Ingest events into Humio
Search Humio events
Humio also has a number of APIs available; meaning there are endless possibilities when it comes to automating Humio workflows with Tines.
Integration with CrowdStrike Falcon, Humio, and Tines
When CrowdStrike, Humio, and Tines are combined, all aspects of security operations and team culture benefit. Everything from alert enrichment to full-cycle incident response (IR) and compliance is enabled and automated. By combining the real-time observability and huge scalability of Humio coupled with the flexibility and intuitive interface of Tines, defenders regain time to move from a reactive to a proactive stance and can deliver a more resilient security posture across their organizational footprint.
To get started with both platforms, sign up for the free Community Editions of Humio and Tines to discover how you can build automation when working with streaming data.