In an ideal approach to zero trust, automation and orchestration are more than useful tools, they’re essential to your agency’s success. You don’t need to take our word for it – security automation and orchestration is mandated by M-22-09 and M-21-31, and forms an integral part of the framework in CISA’s ZTMM (zero trust maturity model).
The message from the government and security experts alike is clear – without automation and orchestration, there is no zero trust.
There are lots of areas where automation can come into play — I think we’re going to fail if we don’t automate as we implement zero trust.
While it's true that CISA recommends a “gradual evolution” to zero trust, automation and orchestration are listed as one of the first steps. But that doesn't mean you have to start automating overnight. It’s important to spend some time defining your automation and orchestration strategy and finding the right tools to help you execute it.
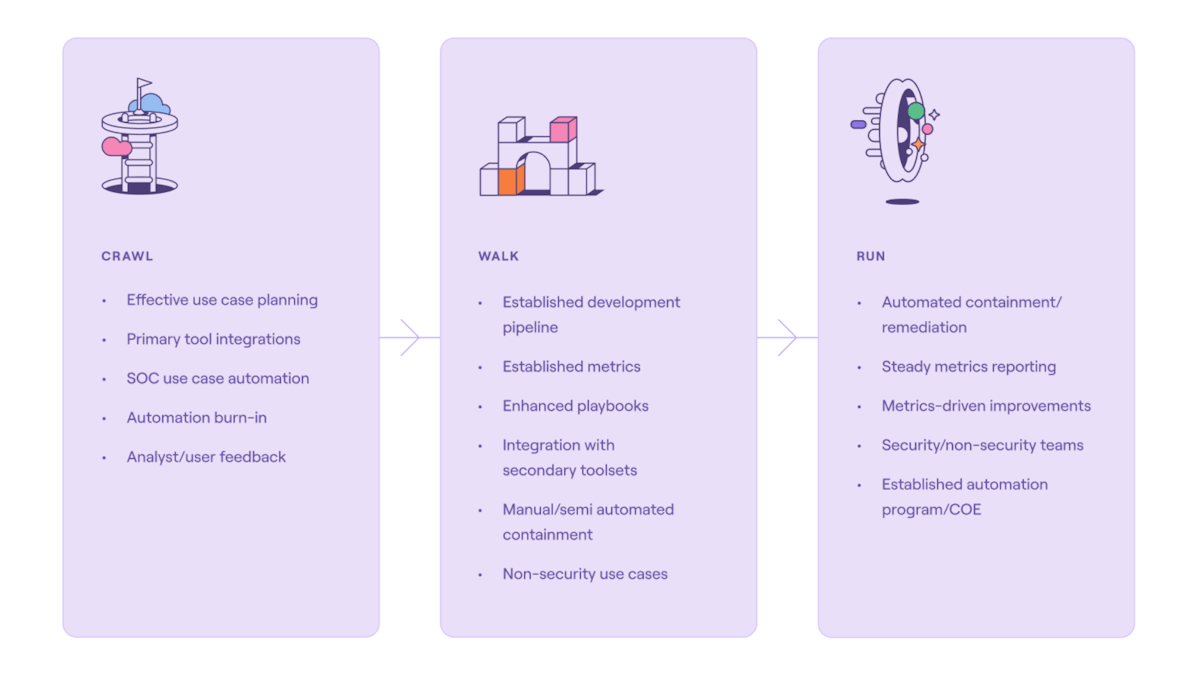
“I try to take the approach of crawl, walk, run into zero trust. You don't have to rip out everything and start over. You can be compliant with the requirements by understanding what you have deployed, and doing an internal exercise to understand what you have in place that can cover the zero trust pillars. Then you can decide what systems you need to supplement that.”
John Harmon, ex-NSA analyst and current RVP of Cyber Solutions at Elastic
Choosing your approach
You can’t buy zero trust, and vendors that promise this should be treated with caution. When it comes to choosing an automation platform, it’s crucial to establish, in as much detail as possible, what you need your platform to do before considering your options.
The truth is, many traditional SOAR platforms are underutilized because they don’t fulfill the organization’s needs, or there aren’t sufficient resources to support them. The problem of software becoming shelfware is well represented in data - in one study by CSO Online, security leaders reported that they only use 72% of the security technologies that they purchase.
This is one of many reasons why federal agencies are moving away from legacy SOAR and towards vendor-agnostic automation platforms like Tines.
Challenges with legacy SOAR
Difficult and time-consuming to learn and deploy (steep learning curve).
Requires engineers or development teams to build and manage workflows (code-based and non-intuitive).
Long build times – playbooks can take weeks to create when they could take hours (coding library dependent).
Lacking a relentless focus on automation and orchestration with limited integrations – it's often a bolted-on feature in a bigger system, e.g., SIEM and TIP platforms.
Limited ability to connect to internal or external tools without a long wait time or added cost due to reliance on apps for integrations and vendor development cycles.
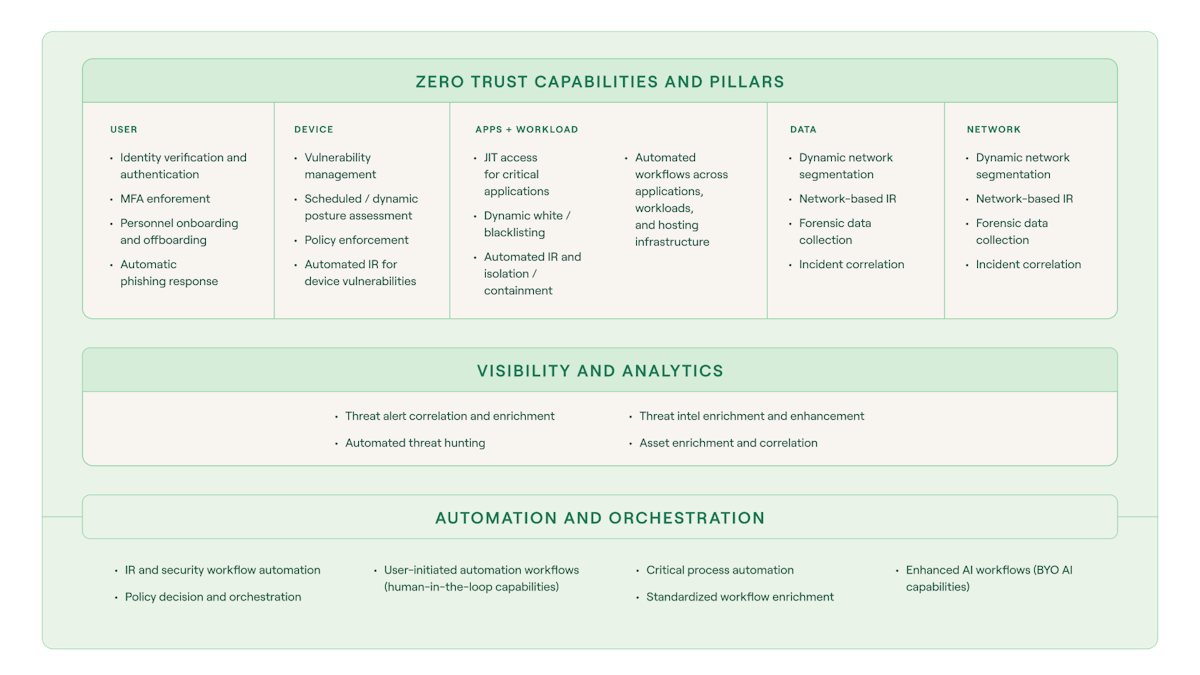
To truly support zero trust, automation must be accessible, flexible, and scalable – enabling not just security teams, but stakeholders across IT, compliance, and operations to contribute to and benefit from orchestrated defense. Making automation work across the agency means focusing on simplicity and adaptability from day one.
Rather than expecting fully autonomous systems out of the gate, successful organizations adopt a crawl-walk-run approach to automation. Starting with small, high-impact workflows and iterating over time builds confidence and maturity. A solid foundation helps teams scale automation across the enterprise without introducing unnecessary risk or complexity.
When choosing an automation strategy, agencies should consider the broader landscape – not just re-purposed and app-based SOAR platforms traditionally designed for security operations centers, but vendor-agnostic automation platforms that support a wider range of zero trust use cases and integrations.
A few things to consider
Every agency has its own unique needs and priorities, but the list above highlights some of the key benefits of leveraging a vendor-agnostic automation platform vs re-purposing a traditional SOAR product for zero trust architectures.
The right-fit platform will be the connective tissue of your zero trust architecture, creating a unified defense strategy by extracting data from disparate tools across the entire organization and orchestrating responses to potential threats.
Automation platform evaluation
Visual workflow editor. Is the product designed for the intuitive building of automation workflows?
Automation scalability. Does it allow for scaling automations outside of security?
Out-of-the-box supported integrations. Does it integrate with our entire tech stack from day one?
Hosting type (on-premise vs cloud). Is the product quick to deploy, and does it have flexible hosting architectures?
Custom code capabilities. Can I leverage coding capabilities when needed?
Licensing model. Does it support scaling our automations when needed?
Easy-to-navigate UI. Does it allow for simplified interactions with automation workflows, keeping humans in the loop for manual to semi-automated workflows?
Automation planning: A framework for faster ROI and adoption
Tines for zero trust
Tines stands out from other automation solutions because of its intuitive and flexible design and ability to connect to any system, internal or external.
Unlike traditional SOAR platforms, Tines offers a no-code or low-code interface that the whole team can use – there’s no need to wait for a developer to build or edit workflows or integrations, and no chance that it will become shelfware.
The platform’s flexible approach to integrations makes it easy to connect to virtually any tool with an API – security, IT, identity, or otherwise. This means agencies can automate across their entire tech stack, not just within traditional security tooling.
It’s especially valuable in zero trust environments, where architectures, systems, and tools are constantly evolving. Tines adapts seamlessly to these changes – whether you're replacing endpoint tools, shifting identity providers, or adding new controls.
Capabilities like “cURL to Tines” or the “API to anything” model allow users to quickly build integrations, and build, maintain, and scale workflows as systems change. As one customer put it, “No matter how many tools you change, you can keep Tines in place.”
Tines’ workflow interface, or “storyboard,” is both documentation and automation. From action descriptions and annotations to viewer roles, there’s little to no need for external documentation. It’s all in-line and legible from the storyboard. This drives consistency and helps compliance with executive orders, particularly when combined with a next-gen SIEM like Elastic.
Why federal agencies choose Tines
Built for mission-critical automation
Fast, easy implementation
Designed for the whole team to use – anyone can build and manage workflows
Integrates with any tool, internal or external, that offers an API
Flexible deployment – cloud, hybrid, or on-premise
Adaptable to changes in your tech stack
Provides the controls you need to reinforce your security posture
Documentation capabilities drive consistency and aid compliance
Capable of handling complex automation workflows
Allows teams to still use code when it's needed
Easy workflow interaction features for non-Tines users
AI, your way
Bring your own AI models to drive secure, mission-ready workflows
Keep humans in the loop with products like Tines Workbench
Accelerate use case development across all zero trust pillars
Enhance response and analysis with AI-powered automation
Achieve zero trust advanced targets with AI-powered features
Operationalize automation in your zero trust architecture with Tines
Tines users can choose from over a thousand pre-built playbooks to import and customize to meet their agency’s needs. Let’s take a look at some popular use cases and workflows for federal agencies pursuing zero trust.
Pre-built workflows
Monitor application access changes in Okta
Tools: Okta


Discover and monitor unmanaged devices using Axonius
Tools: Axonius, Jira Software, Shodan

Block suspicious IPs by creating firewall rule groups with CrowdStrike
Tools: CrowdStrike, Slack
Investigate & remediate critical container vulnerabilities in Aqua Security Cloud Workload Protection Platform
Tools: Aqua Security, Jira Software

Implement data loss prevention policies
Tools: Google, Panther, Slack


Want to explore more? Browse our library of pre-built playbooks for asset and app management, employee lifecycle management, incident and alerts, and more.
Getting started with Tines for zero trust
Visit tines.com/federal to learn how Tines can help your agency operationalize automation and achieve zero trust goals
Want to try it out? Sign up for our free Community Edition to start building today: tines.com/community-edition
Ready to connect? Visit tines.com/book-a-demo to speak to a member of our federal team