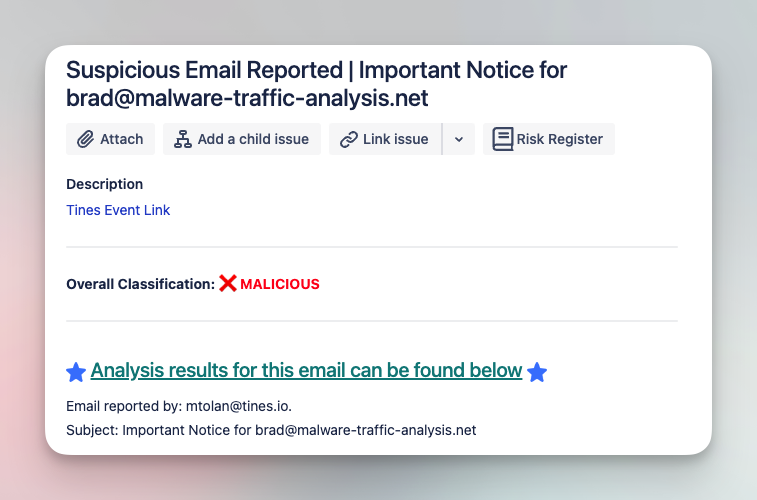
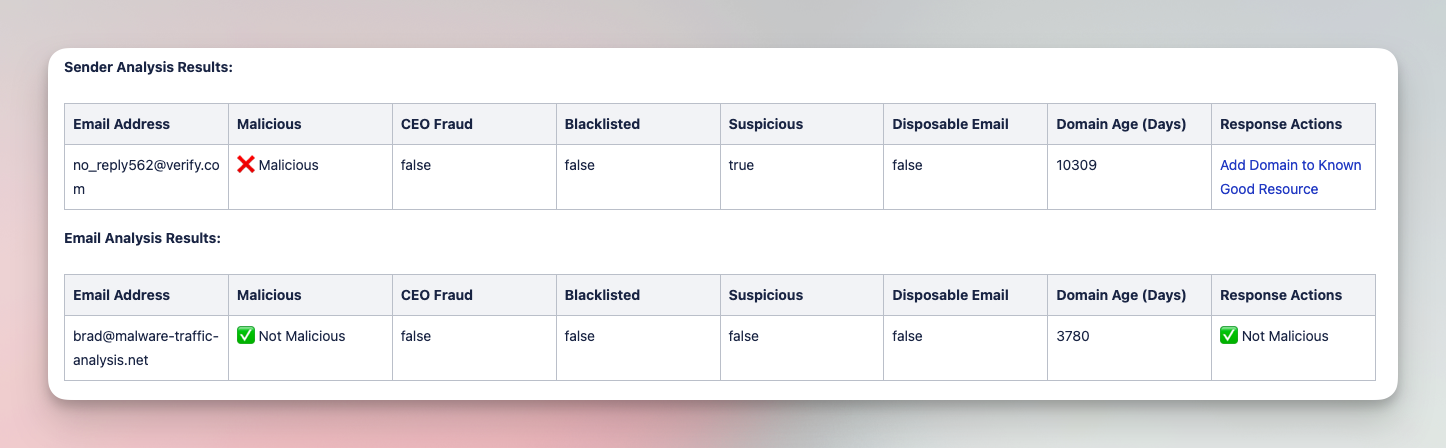
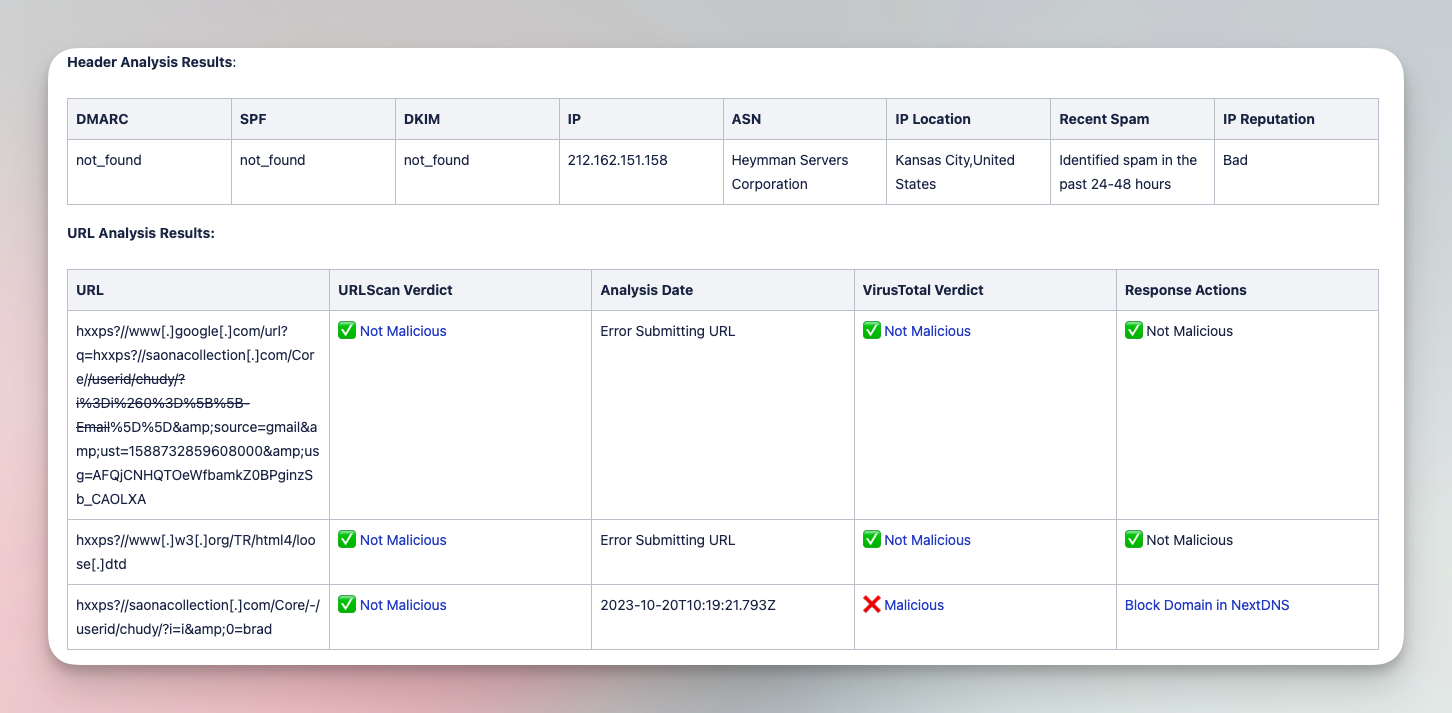
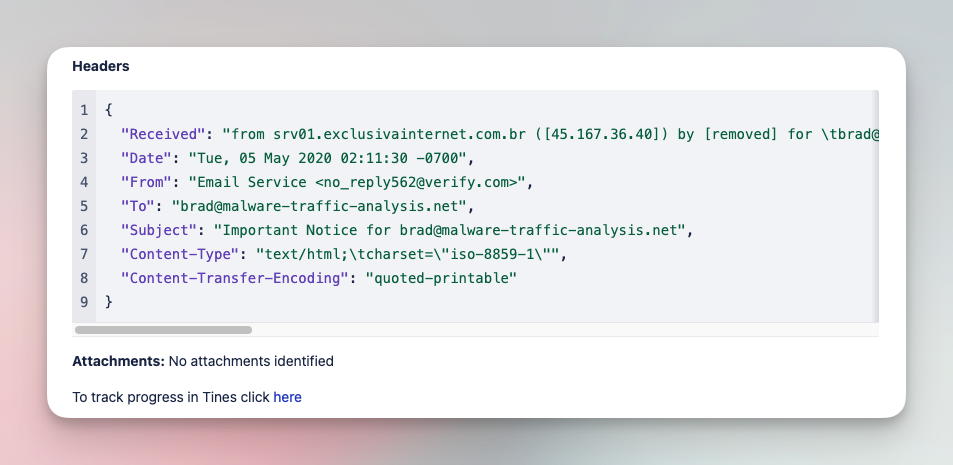
Analyze and triage suspicious emails with various tools
Submit suspicious emails and investigate with a comprehensive analysis of files, URLs, and headers. Add IOCs to various tool blocklists in order to limit impact of phishing campaigns.
Tools
CrowdStrike, EmailRep, Jira Software, NextDNS, URLScan.io, VirusTotal
Created by
Michael Tolan
How it works
Import this story to your tenant, from where you can adapt it to meet your unique needs.
ImportWas this story helpful?