Command-over-HTTP allows your Tines tenant to make programmatic calls to systems running on your private network, which may not have HTTP interfaces.
It is deployed as a container service within your network, and has the capability to execute python, bash, and powershell scripts there.
Deployment
Command-over-HTTP is available with the tunnel add-on option for cloud customers, and included for self-hosted customers. To get started, reach out to us and we will enable for your tenant.
Once enabled, visit https://<your-tenant-domain>/admin/command-over-http to obtain your deployment credentials. Only tenant owners or users with the TUNNEL_MANAGE tenant permission can access this page.
The container can be run through various orchestration platforms, for example Docker:
docker run \
-d \
--name command-over-http \
--env TINES_TUNNEL_SECRET="secret" \
tines/command-over-http:latestFor self-hosted customers, this can be configured without the TINES_TUNNEL_SECRET variable to communicate within your hosted platform setup and not via Cloudflare.
docker run \
-d \
--name command-over-http \
tines/command-over-http:latestUsage
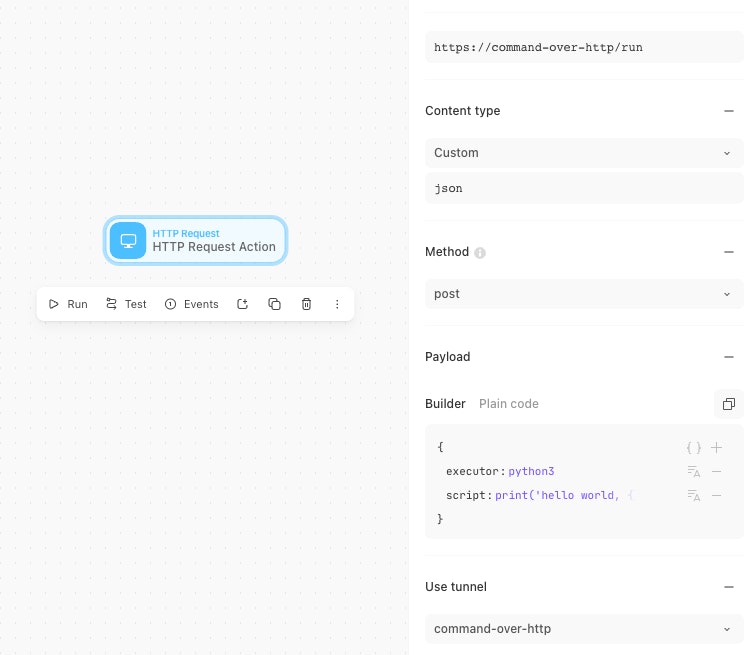
Once enabled and deployed, use the HTTP request action to call the module. To do this, enable the ‘use tunnel’ parameter, and target the special URL https://command-over-http/run.
Finally, pass a JSON payload containing two keys: 1) executor (python3, powershell, or bash) and 2) script (the command or script you want to execute).
If you do choose to override the hostname when running the container, ensure the tenant can reach the container at the correct hostname via the HTTP action.