Good credential management is critical when working with APIs. Not only do credentials need to be secure, but they also need to be accessible for use. Tines can store many different kinds of credentials like basic text credentials, OAuth credentials, and AWS credentials. One of the most flexible credential types is the HTTP Request action credential (HRAC). This type of credential allows users to dynamically authenticate to APIs that might have multiple legs of their authentication or retrieve passwords from secure privilege access managers.
Simple Authentication Tokens
TruStar is a threat intelligence platform that uses multiple API requests for authentication and returns time-limited tokens. If a basic text credential was used to store our authentication info, that credential would need to be rotated quite often. Instead of suffering that burden, using the HRAC, Tines can refresh authentication credentials when needed. Take a look at this example:
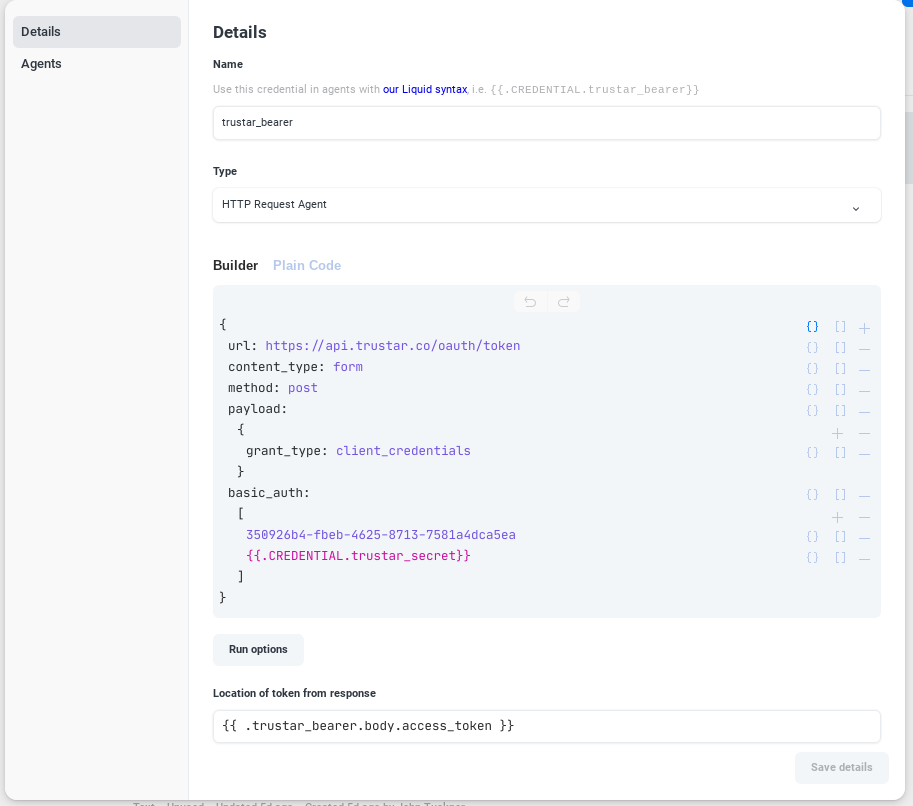
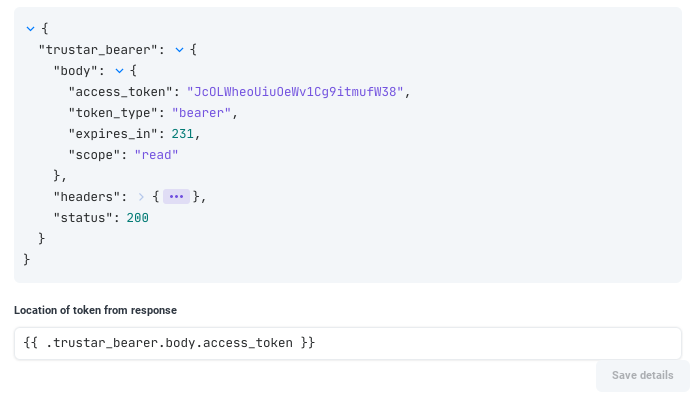
We've created an HRAC that will request a token from TruStar when we give it some authentication parameters. Using "Run Options", the HTTP request above will be made and then results will be shown. Then we can identify where the authentication token is in the "Location of token from response" field, referencing fields of the response like on the Tines Storyboard.
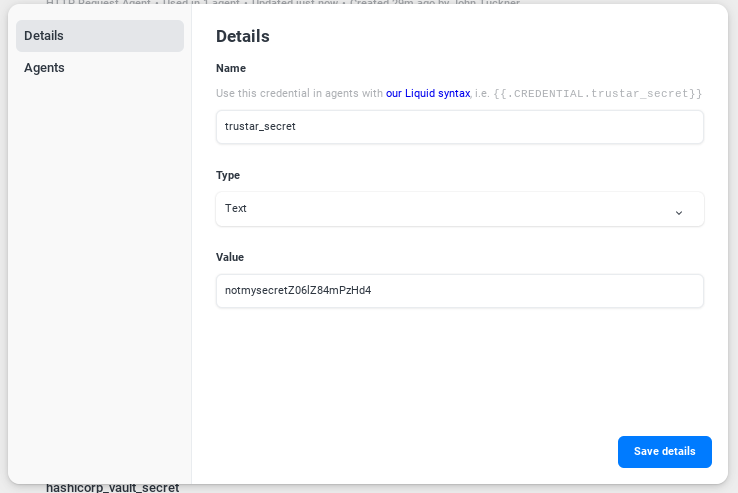
You'll also notice, that we're able to reference another credential, our TruStar secret, in the HRAC. We can store that secret separately so it doesn't appear in the HRAC and we can rotate that credential separately if needed.
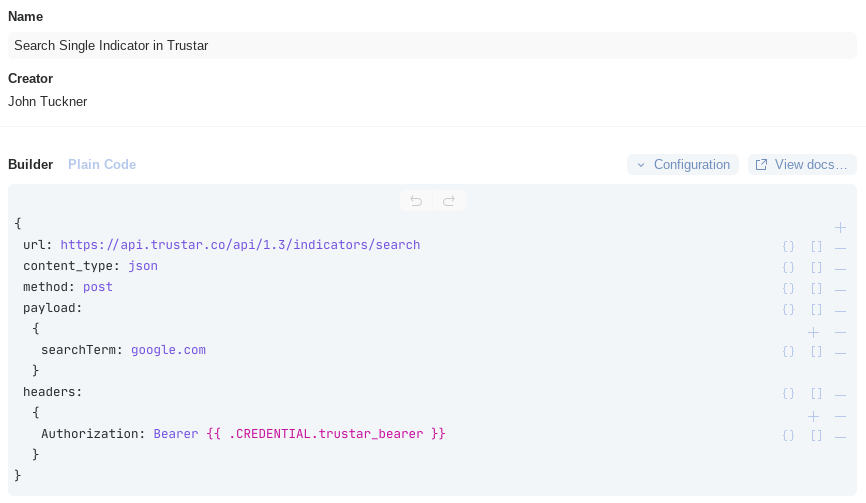
Once the HRAC is set up, we can use it like we would any other credential in actions on the Tines Storyboard. In the below example, we use the token to authorize a call to TruStar's indicator search.
Password Vaults
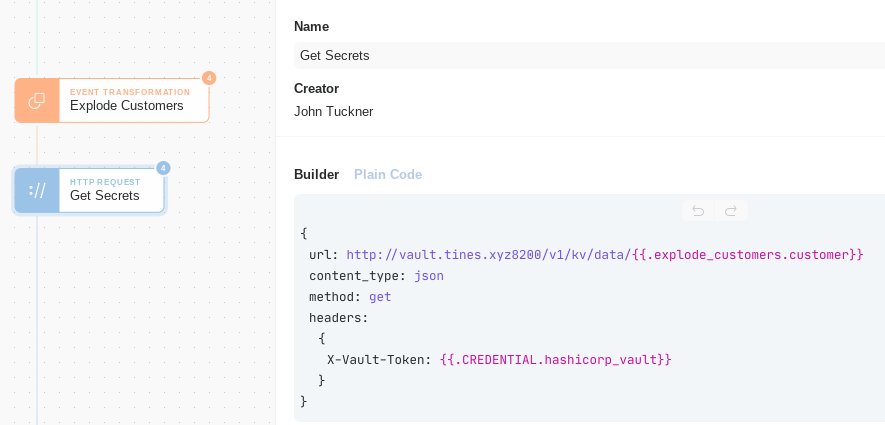
Privileged access management and password vaults are becoming increasingly more common as identity tokens become more prevalent. Managed service providers also need an outlet to manage a large number of credentials for their clients safely. Using the HRAC, Tines can enable many password vault solutions. Take a look at how one would access HashiCorp Vault in Tines:
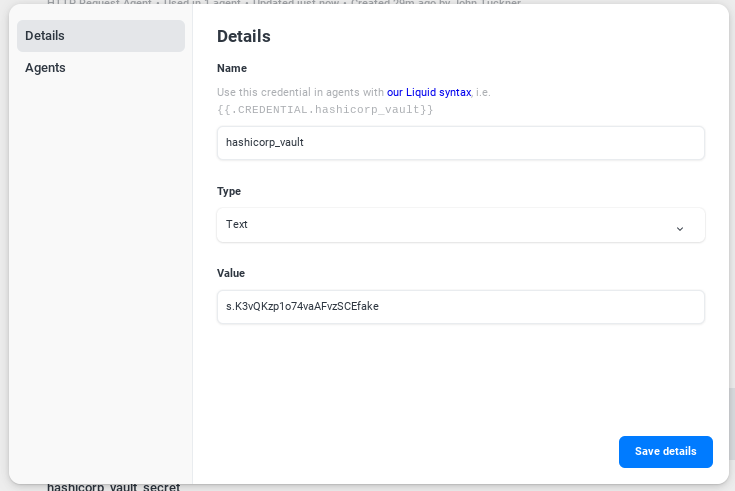
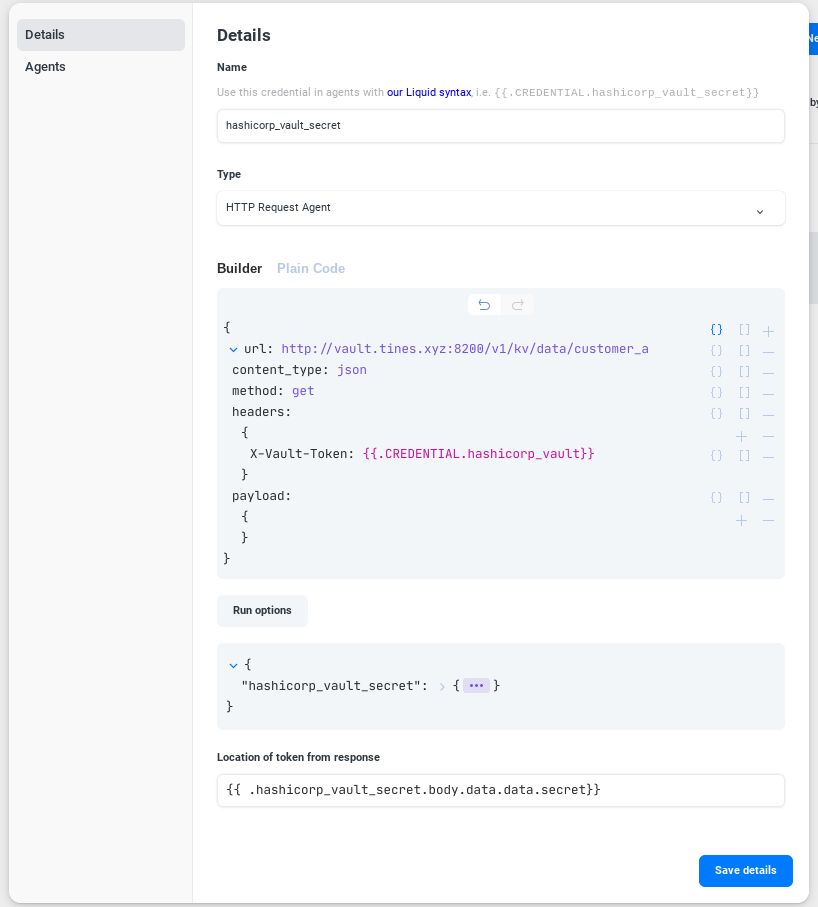
We'll again create a basic text credential with the token we need to access the vault. Then, we'll create an HRAC to access HashiCorp Vault to get a secret stored there in its key/value storage. In this example, we'll get the secrets for a single customer named "customer_a":
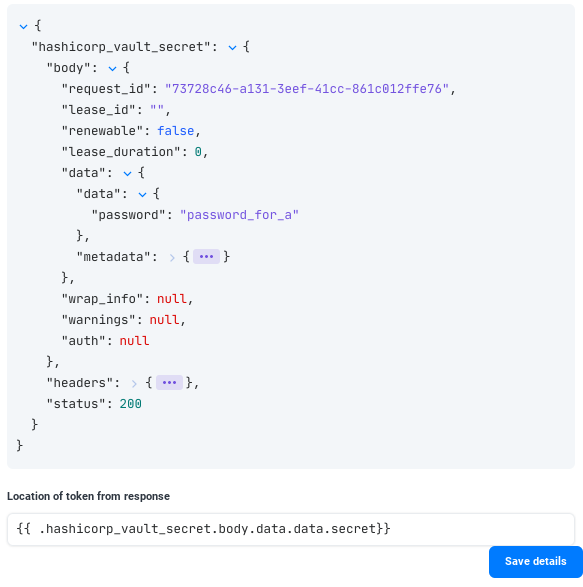
In the body of the response, we'll see that the password "password_for_a" is returned and we can reference it easily:
A small drawback to the HRAC is that it does not support passing variables or iterating over arrays at this time (we hardcoded "customer_a" in the above example). What if you had a list of customers with data you'd like to access?
Well, the fallback is to just use the HRAC the way they worked in the past.... simply add an HTTP Request Action to the Tines Storyboard and it will work the same as the HRAC created in the Credentials tab!